wikiHow is a “wiki,” similar to Wikipedia, which means that many of our articles are co-written by multiple authors. To create this article, 27 people, some anonymous, worked to edit and improve it over time.
The wikiHow Tech Team also followed the article's instructions and verified that they work.
This article has been viewed 1,375,909 times.
Learn more...
If you're connecting to a Unix system over the internet, it's important to encrypt your connection so your passwords and other data remain secure. An easy way to do this is to install an SSH client on your computer and use that to make a command-line connection. This wikiHow article will teach you how to install an SSH client on Windows (as Linux and macOS already have SSH), and how to connect to a remote host with a secure shell.
Steps
Connecting for the First Time
-
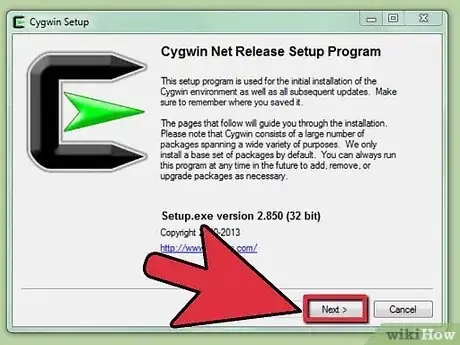
1Install SSH. For Windows, you will need to download and install an SSH client program. The most popular one is Cygwin, which is available for free from the developer’s website. Download and install it like you would any other program. Another popular free program is PuTTY.
- During the Cygwin installation, you must choose to install OpenSSH from the Net section.
- Linux and Mac OS X come with SSH already installed on the system. This is because SSH is a UNIX system, and Linux and OS X are derived from UNIX.
- If you have Windows 10 with the Anniversary Update, you can install the Windows Subsystem for Linux which comes with SSH preinstalled.
-
2Run SSH. Open the terminal program that is installed by Cygwin, or Bash on Ubuntu on Windows for Windows 10, or open the Terminal in OS X or Linux. SSH uses the terminal interface to interact with other computers. There is no graphical interface for SSH, so you will need to get comfortable typing in commands.Advertisement
-
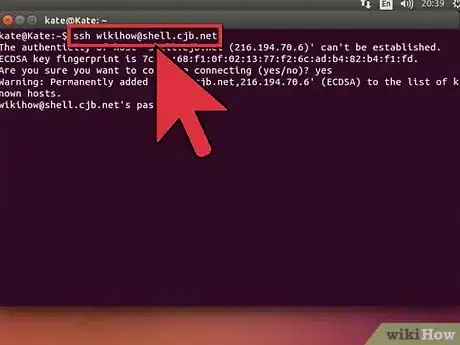
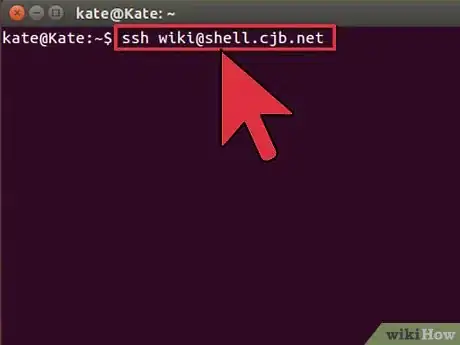
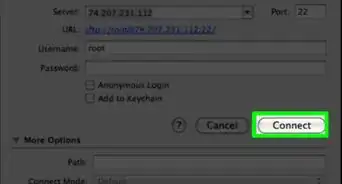
3Test the connection. Before you dive into creating secure keys and moving files, you’ll want to test that SSH is properly configured on your computer as well as the system you are connecting to. Enter the following command, replacing <username> with your username on the remote computer, and <remote> with the address for the remote computer or server:
$ ssh <username>@<remote>- If you want to specify a port, add
-p 0000, (replace 0000 with the desired port number). - You will be asked for your password once the connection is established. You will not see the cursor move or any characters input when you type your password.
- If this step fails, then either SSH is configured incorrectly on your computer or the remote computer is not accepting SSH connections.
Learning Basic Commands
-
1Navigate the SSH shell. When you first connect to the remote computer, you should be located in your HOME directory. To move around the directory structure, use the
cdcommand:[1]-
cd ..will move you up one directory. -
cd <directoryname>will move you into the specified subdirectory. -
cd /home/directory/path/will move you into the specified directory from the root (home). -
cd ~will return you to your HOME directory.
-
-
2Check your current directory's contents. To see what files and folders in your current location, you can use the
lscommand:[2]-
lswill list all of the files and folders in your current directory. -
ls –lwill list the contents of the directory along with additional information such as size, permissions, and date. -
ls-awill list all the contents including hidden files and folders.
-
-
3Copy files from your location to the remote computer. If you need to copy files from your local computer to the computer you are accessing remotely, you can use the
scpcommand:-
scp /localdirectory/example1.txt <username>@<remote>:<path>will copy example1.txt to the specified <path> on the remote computer. You can leave <path> blank to copy to the root folder of the remote computer. -
scp <username>@<remote>:/home/example1.txt ./will move example1.txt from the home directory on the remote computer to the current directory on the local computer.
-
-
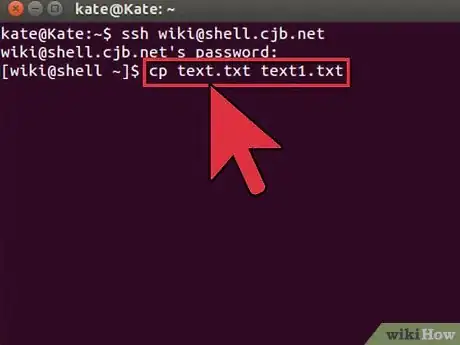
4Copy files through the shell. You can use the
cpcommand to make copies of files either in the same directory or into a directory of your choosing:-
cp example1.txt example2.txtwill create a copy of example1.txt called example2.txt in the same location. -
cp example1.txt <directory>/will create a copy of example1.txt in the location specified by <directory>.
-
-
5Move and rename files. If you want to change a file’s name or move it without copying, you can use the
mvcommand:-
mv example1.txt example2.txtwill rename example1.txt to example2.txt. The file will stay in the same location. -
mv directory1 directory2will rename directory1 to directory2. The directory’s contents will remain unchanged. -
mv example1.txt directory1/will move example1.txt into directory1. -
mv example1.txt directory1/example2.txtwill move example1.txt into directory1 and rename it to example2.txt
-
-
6Delete files and directories. If you need to remove anything from the computer you are connected to, you can use the
rmcommand:-
rm example1.txtwill delete the file example1.txt. -
rm –I example1.txtwill delete the file example1.txt after prompting you to confirm. -
rm directory1/will delete directory1 and all of its contents.
-
-
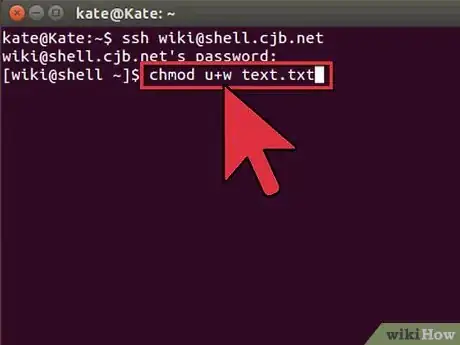
7Change permissions for your files. You can change the read and write privileges of your files using the
chmodcommand:-
chmod u+w example1.txtwill add the write (modify) permission to the file for the user (u). You can also use thegmodifier for group permissions or theofor world permissions. -
chmod g+r example1.txtwill add the read (access) permission to the file for the group. - There are a large list of permissions that you can use to secure or open various aspects of your system.[3]
-
-
8Learn the other assorted basic commands. There are a few more important commands that you will be using quite a bit in the shell interface. They include:
-
mkdir newdirectorywill create a new subdirectory called newdirectory. -
pwdwill display your current directory location. -
whoshows who is logged into the system. -
pico newfile.txtorvi newfile.txtwill create a new file and open the file editor. Different system will have different file editors installed. The most common are pico and vi. You may need to use different commands if you have a different file editor installed.
-
-
9Get detailed information on any command. If you are unsure as to what a command will do, you can use the
mancommand to learn about all of the possible uses and parameters:-
man <command>will display information about that command. -
man –k <keyword>will search all of the man pages for the keyword you specify.[4]
-
Creating Encrypted Keys
-
1Create your SSH keys. These keys will allow you to connect to the remote location without having to enter your password each time. This is a much more secure way to connect to the remote computer, as the password will not have to transmitted over the network.
- Create the key folder on your computer by entering the command
$ mkdir .ssh - Create the public and private keys by using the command
$ ssh-keygen –t rsa - You will be asked if you would like to create a passphrase for the keys; this is optional. If you don’t want to create a passphrase, press Enter. This will create two keys in the .ssh directory: id_rsa and id_rsa.pub
- Change your private key’s permissions. In order to ensure that the private key is only readable by you, enter the command
$ chmod 600 .ssh/id_rsa
- Create the key folder on your computer by entering the command
-
2Place the public key on the remote computer. Once your keys are created, you’re ready to place the public key on the remote computer so that you can connect without a password. Enter the following command, replacing the appropriate parts as explained earlier:
$ scp .ssh/id_rsa.pub <username>@<remote>:- Make sure to include the colon (:) at the end of the command.
- You will be asked to input your password before the file transfer starts.
-
3Install the public key on the remote computer. Once you’ve placed the key on the remote computer, you will need to install it so that it works correctly. First, log in to the remote computer the same way that you did in Step 3.
- Create an SSH folder on the remote computer, if it does not already exist:
$ mkdir .ssh - Append your key to the authorized keys file. If the file does not exist yet, it will be created:
$ cat id_rsa.pub >> .ssh/authorized_keys - Change the permissions for the SSH folder to allow access:
$ chmod 700 .ssh
- Create an SSH folder on the remote computer, if it does not already exist:
-
4Check that the connection works. Once the key has been installed on the remote computer, you should be able to initiate a connection without being asked to enter your password. Enter the following command to test the connection:
$ ssh <username>@<remote>- If you connect without being prompted for the password, then the keys are configured correctly.
Community Q&A
-
QuestionHow can I use the SCP command when using Windows Power Shell Open SSH? I am remoting an Ubuntu 16.04 VPS. It still asks for my password.
 Aiden MartinezCommunity AnswerIf you try to use Powershell on a non-admin account, it will request a password. Try typing in your account password if you're the admin.
Aiden MartinezCommunity AnswerIf you try to use Powershell on a non-admin account, it will request a password. Try typing in your account password if you're the admin. -
QuestionWhat if I need to access a certain port?
 Community AnswerUse flag-p, followed by the port number. For example: @ -p
Community AnswerUse flag-p, followed by the port number. For example: @ -p
References
About This Article
To use SSH, start by downloading and opening SSH if you have Windows, or simply opening it if you have a Mac or Linux system. Then, enter the command “$ ssh,” your username on the remote computer, followed by the computer or server's address. Next, enter the command “cd . .” to move up 1 directory, or “cd < directoryname >” to move into a subcategory. You can also use the command “ls” to list all of the files and folders in the current directory. For tips on how to set up encryption keys, read on!