An easy-to-follow guide on being your own CA
X
wikiHow is a “wiki,” similar to Wikipedia, which means that many of our articles are co-written by multiple authors. To create this article, 21 people, some anonymous, worked to edit and improve it over time.
This article has been viewed 156,611 times.
Learn more...
Getting an SSL certificate from any of the major Certificate Authorities (CAs) can run $100 and up. Add to the mix, news stories which seem to indicate that not all of the established CAs can be trusted 100% of the time and you might decide to circumvent the uncertainty and erase the cost by being your own Certificate Authority.
Steps
Part 1
Part 1 of 4:
Creating your CA Certificate
-
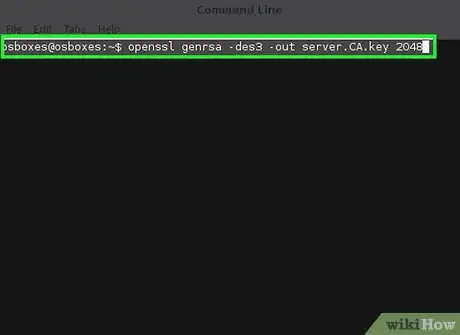
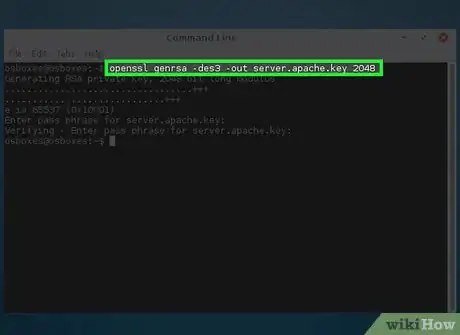
1Generate your CA's private key by issuing the following command.
openssl genrsa -des3 -out server.CA.key 2048- The options explained
- openssl - the name of the software
- genrsa - creates a new private key
- -des3 - encrypt the key using the DES cipher
- -out server.CA.key - the name of your new key
- 2048 - the length, in bits, of the private key (Please see the warnings)
- Store this certificate and the password in a safe place.
-
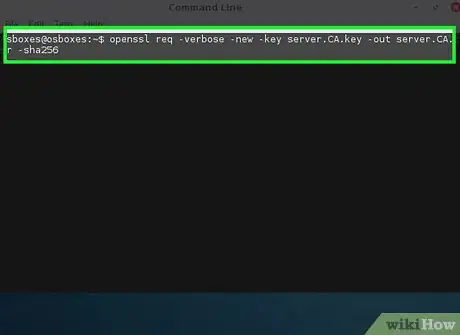
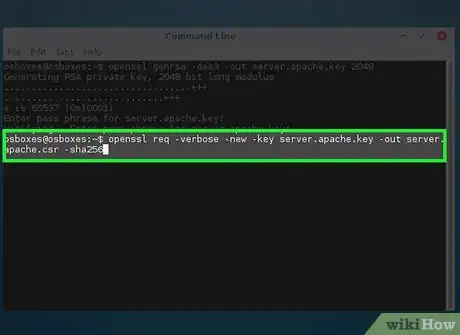
2Create a certificate signing request.
openssl req -verbose -new -key server.CA.key -out server.CA.csr -sha256- The options explained:
- req - Creates a Signing Request
- -verbose - shows you details about the request as it is being created (optional)
- -new - creates a new request
- -key server.CA.key - The private key you just created above.
- -out server.CA.csr - The file name of the signing request you are creating
- sha256 - The encryption algorithm to use for signing requests (If you don't know what this is, do not change this. You should only change this if you know what you are doing)
Advertisement -
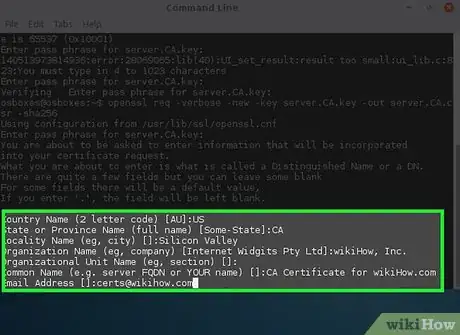
3Fill out the information as much as possible.
Country Name (2 letter code) [AU]: US- State or Province Name (full name) [Some-State]: CA
- Locality Name (e.g., city) []: Silicon Valley
- Organization Name (e.g., company) [Internet Widgits Pty Ltd]: wikiHow, Inc.
- Organizational Unit Name (eg, section) []:
- Common Name (e.g., server FQDN or YOUR name) []: CA Certificate for wikiHow.com
Email Address []: certs@wikihow.com
-
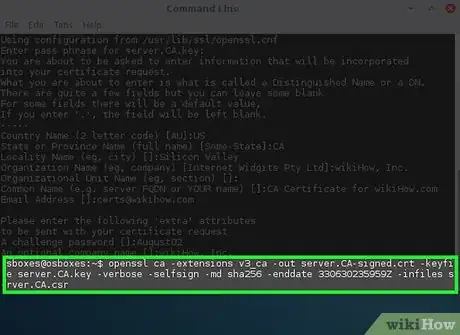
4Self-sign your certificate:
openssl ca -extensions v3_ca -out server.CA-signed.crt -keyfile server.CA.key -verbose -selfsign -md sha256 -enddate 330630235959Z -infiles server.CA.csr- The options explained:
- ca - Loads the Certificate Authority module
- -extension v3_ca - Loads the v3_ca extension, a must-have for use on modern browsers
- -out server.CA-signed.crt - The name of your new signed key
- -keyfile server.CA.key - The private key you created in step 1
- -verbose - shows you details about the request as it is being created (optional)
- -selfsign - Tells openssl that you are using the same key to sign the request
- -md sha256 - The encryption algorithm to use for the message. (If you don't know what this is, do not change this. You should only change this if you know what you are doing)
- -enddate 330630235959Z - The end date of the certificate. The notation is YYMMDDHHMMSSZ where Z is in GMT, sometimes known as "Zulu" time.
- -infiles server.CA.csr - the signing request file that you created the step above.
-
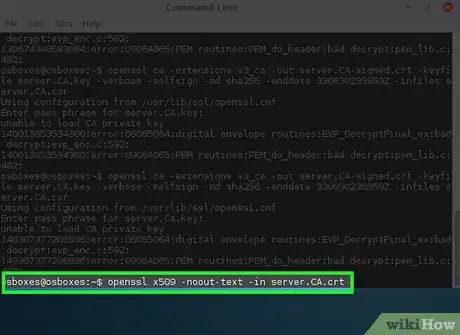
5Inspect your CA certificate.
- openssl x509 -noout -text -in server.CA.crt
- The options explained:
- x509 - Loads the x509 module to inspect signed certificates.
- -noout - Do not output the encoded text
- -text - output the information on the screen
- -in server.CA.crt - Load the signed certificate
- The server.CA.crt file can be distributed to anyone who will use your website or use certificates that you plan on signing.
Advertisement
Part 2
Part 2 of 4:
Creating SSL Certificates for a Service, such as Apache
-
1Create a private key.
openssl genrsa -des3 -out server.apache.key 2048- The options explained:
- openssl - the name of the software
- genrsa - creates a new private key
- -des3 - encrypt the key using the DES cipher
- -out server.apache.key - the name of your new key
- 2048 - the length, in bits, of the private key (Please see the warnings)
- Store this certificate and the password in a safe place.
-
2Create a certificate signing request.
openssl req -verbose -new -key server.apache.key -out server.apache.csr -sha256- The options explained:
- req - Creates a Signing Request
- -verbose - shows you details about the request as it is being created (optional)
- -new - creates a new request
- -key server.apache.key - The private key you just created above.
- -out server.apache.csr - The file name of the signing request you are creating
- sha256 - The encryption algorithm to use for signing requests (If you don't know what this is, do not change this. You should only change this if you know what you are doing)
-
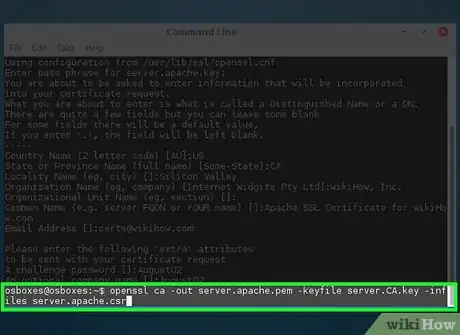
3Use your CA certificate to sign the new key.
openssl ca -out server.apache.pem -keyfile server.CA.key -infiles server.apache.csr- The options explained:
- ca - Loads the Certificate Authority module
- -out server.apache.pem - The file name the signed certificate
- -keyfile server.CA.key - The file name of the CA certificate that will be signing the request
- -infiles server.apache.csr - The file name of the Certificate Signing Request
-
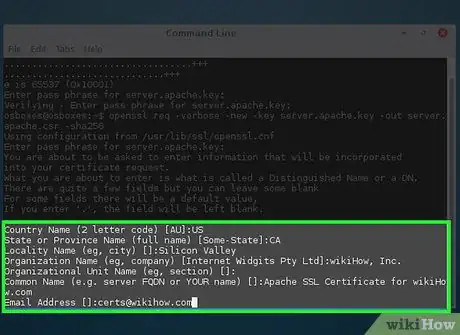
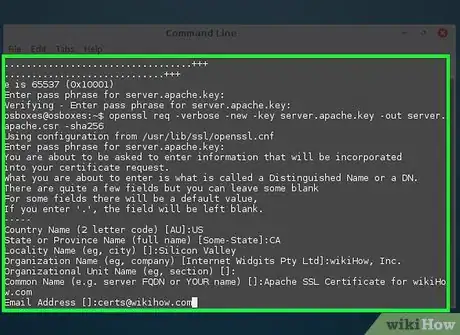
4Fill out the information as much as possible:
Country Name (2 letter code) [AU]: US- State or Province Name (full name) [Some-State]: CA
- Locality Name (e.g., city) []: Silicon Valley
- Organization Name (e.g., company) [Internet Widgits Pty Ltd]: wikiHow, Inc.
- Organizational Unit Name (eg, section) []:
- Common Name (e.g., server FQDN or YOUR name) []: Apache SSL Certificate for wikiHow.com
Email Address []: certs@wikihow.com
-
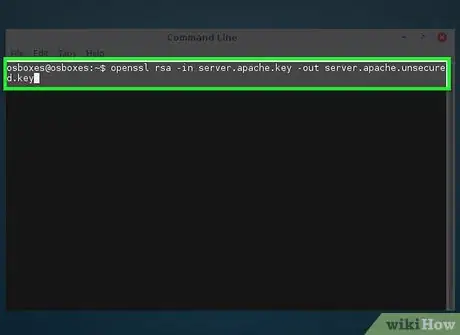
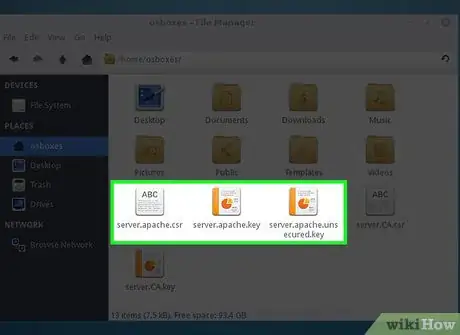
5Save a copy of your private key in another location. Create a private key without a password to prevent Apache from prompting you for a password:
openssl rsa -in server.apache.key -out server.apache.unsecured.key- The options explained:
- rsa - Runs the RSA encryption program
- -in server.apache.key - The key name that you want to convert.
- -out server.apache.unsecured.key - The file name of the new unsecured key
-
6Use the resulting server.apache.pem file along with the private key you generated in step 1 to configure your apache2.conf file.
Advertisement
Part 3
Part 3 of 4:
Creating a User Certificate for Authentication
Part 4
Part 4 of 4:
Creating S/MIME E-mail Certificates
-
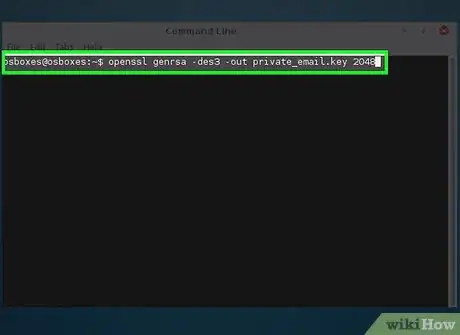
1Create a private key.
- openssl genrsa -des3 -out private_email.key 2048
-
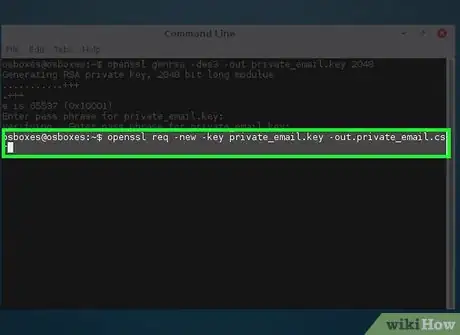
2Create a Certificate Signing Request.
- openssl req -new -key private_email.key -out private_email.csr
-
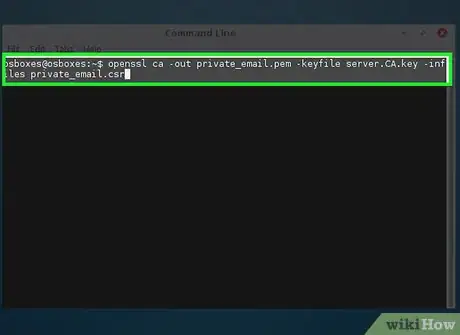
3Use your CA certificate to sign the new key.
- openssl ca -out private_email.pem -keyfile server.CA.key -infiles private_email.csr
-
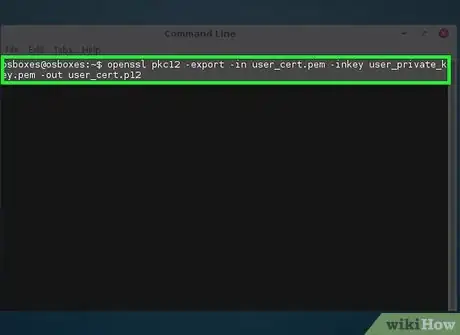
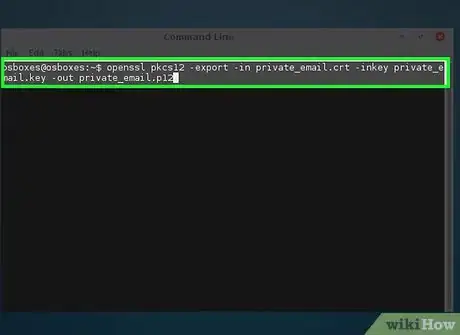
4Convert the certificate to PKCS12.
- openssl pkcs12 -export -in private_email.crt -inkey private_email.key -out private_email.p12
-
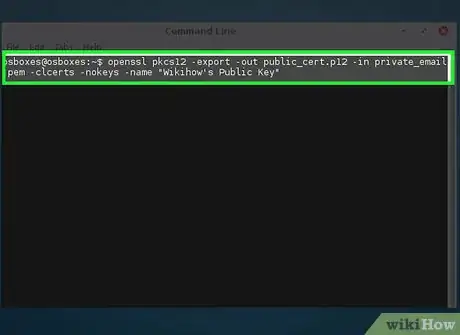
5Create a Public Key certificate for distribution.
- openssl pkcs12 -export -out public_cert.p12 -in private_email.pem -clcerts -nokeys -name "WikiHow's Public Key"
Advertisement
Community Q&A
-
QuestionHow would I complete this on Windows?
 Community AnswerYou need open SSL for Windows. There are various projects out there on the web offering such binaries and installers. Please Google it!
Community AnswerYou need open SSL for Windows. There are various projects out there on the web offering such binaries and installers. Please Google it! -
QuestionOnce I have set up my own CA, how do I add it to browsers, Java, and other apps, so that they will then trust any server or app certs I signed with my CA cert instead of giving errors?
 Community AnswerYou will need to get together with browser vendors and have them install your certificate on devices. Depending on the vendor, this could require a large sum of money.
Community AnswerYou will need to get together with browser vendors and have them install your certificate on devices. Depending on the vendor, this could require a large sum of money.
Advertisement
Warnings
- 1024-bit keys are considered to be obsolete. 2048-bit keys are considered to be secure for user certificates until 2030, but is considered insufficient for root certificates. Consider these vulnerabilities as you create your certificates.⧼thumbs_response⧽
- By default, most modern browsers will show an "Untrusted certificate" warning when someone visits your site. There has been much debate over the wording of these warnings, as non-technical users can be caught off-guard. It's often best to use a major authority so users do not get the warnings.⧼thumbs_response⧽
Advertisement
Things You'll Need
- Linux distribution with OpenSSL installed
- Terminal access
References
About This Article
Advertisement