wikiHow is a “wiki,” similar to Wikipedia, which means that many of our articles are co-written by multiple authors. To create this article, volunteer authors worked to edit and improve it over time.
This article has been viewed 153,741 times.
Learn more...
This how-to explains a clear and step-by-step, 1-minute process to verify that a file in your possession was digitally signed by a particular GPG Secret Key and has been unmodified since the time of signing.
Steps
Downloading What You Need
To verify your belief that someone has signed a file, you will need a copy of that person's Public Key, a copy of the file, and a copy of the signature-file that was allegedly created through the interaction of the person's Secret Key and the file.
Using GPG to Verify that someone's Secret Key Signed the File in Question
GPG will help you verify the relationship between your three files.
-
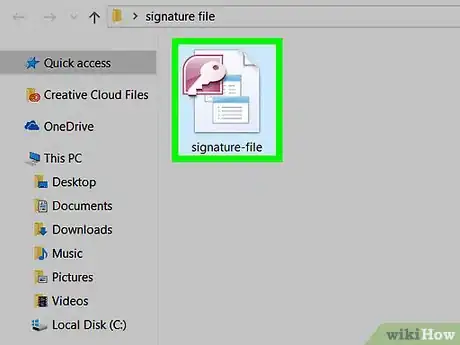
1Open a command-line interface.
- Change the working directory to the Folder where your file and signature-file are saved.
-
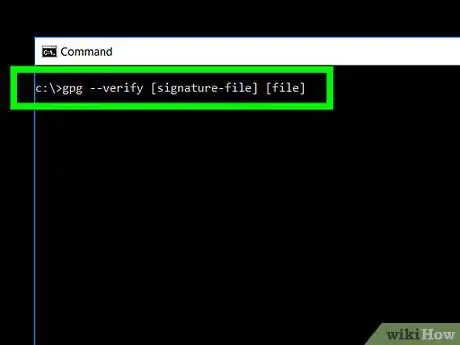
2Verify the signature.
- Type the following command into a command-line interface:
gpg --verify [signature-file] [file]- E.g., if you have acquired
- (1) the Public Key 0x416F061063FEE659,
- (2) the Tor Browser Bundle file (tor-browser.tar.gz), and
- (3) the signature-file posted alongside the Tor Browser Bundle file (tor-browser.tar.gz.asc),
- You would type the following:
gpg --verify tor-browser.tar.gz.asc tor-browser.tar.gz
Community Q&A
-
QuestionThis guide shows how it's done on Windows, how is this done on Linux and macOS? In the same way or is it different?
 Radj307Community AnswerThe method is identical for all platform-specific implementations of the GPG utility.
Radj307Community AnswerThe method is identical for all platform-specific implementations of the GPG utility. -
Question'GPG' is not recognized as an internal or external command, operable program or batch file. What is wrong?
 Radj307Community AnswerYou will need GPG installed to be able to use the GPG command. On Windows, you can use GPG4Win.
Radj307Community AnswerYou will need GPG installed to be able to use the GPG command. On Windows, you can use GPG4Win. -
QuestionHow can I acquire the Public Key in Part 1 for the file targeted for download?
 Radj307Community AnswerThe distributor of the file likely has their PGP public key somewhere on their website.
Radj307Community AnswerThe distributor of the file likely has their PGP public key somewhere on their website.
Warning
- Although you are now certain the Secret Key bound to the Public Key you possess was used to sign the file, you must still take precautions to ensure that this Public Key actually belongs to the person you believe it belongs to. Nothing prevents an adversary from making keys that appear to belong to someone.
- If you have not imported someone's Public Key to your GPG Keyring, this procedure does not work.
- The person may name the signature-file anything they want: the names of the file and the signature-file do not need to be similar or related.
Things You'll Need
- GPG Encryption Engine
- Signed file
- Signature-file
- GPG Public Key