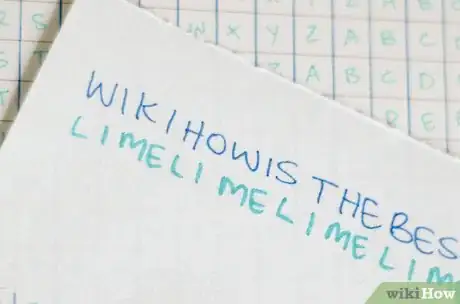wikiHow is a “wiki,” similar to Wikipedia, which means that many of our articles are co-written by multiple authors. To create this article, 42 people, some anonymous, worked to edit and improve it over time.
This article has been viewed 384,812 times.
Learn more...
The Vigenère cipher is a method of encryption that uses a series of different "Caesar ciphers" based on the letters of a keyword. In a Caesar cipher, each letter in the passage is moved a certain number of letters over, to be replaced by the corresponding letter. For example, this would mean that in a Caesar cipher shift of three: A would become D; B would become E; C would become F etc. A Vigenère cipher builds on this method by using multiple Caesar ciphers at different points in the message; this article shows you how to use it.[1]
Steps
Sample Cipher and Messages
Encipher
-
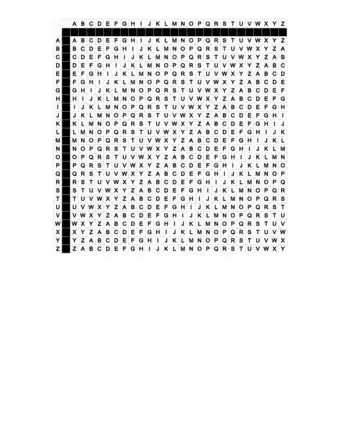
1Obtain a Vigenère Square (see Sample) or create a Vigenère Square on your own.[2]
-
2Think of a keyword that is shorter than the phrase or phrases you want to encipher. For this example we will use:
LIME
[3]Advertisement -
3Write down your message without spaces. For this example, we will use:
WIKIHOWISTHEBEST
[4] -
4Write the keyword under your message, carefully lining each letter up with a letter from your message. Do this until you run out of message:
WIKIHOWISTHEBEST
LIMELIMELIMELIME
[5] -
5Cut the keyword to fit the phrase if needed. In the example used for this article, the word
LIME
fits perfectly but when the keyword is not a perfect fit, there is no need to use the full word. For example:WIKIHOWISTHEBESTOFTHEBEST
LIMELIMELIMELIMELIMELIMEL
-
6Go to the row of the first letter of the keyword in the Vigenère Square and go to the column of the first letter of the actual message and find the intersection point of the row and column. That's your cipher letter.[6]
-
7Continue on in this fashion until your entire phrase is ciphered. Using the sample Vigenère square given above, the first ciphertext letter is an H coming from row L and column W. So the ciphertext is:
HQWMSWIMDBTIMMEX
Decipher
-
1Perform the above steps in reverse to decode ciphered text.[7]
-
2Find the row of the first letter of the keyword. Look along it to find the first letter of the ciphered text in that row. Follow the column up to find the first letter of the encoded phrase at the top of the chart.[8]
-
3Continue on in this manner until you completely decipher the text.
Community Q&A
-
QuestionWhat kind of secret texting uses double letters, capital and lowercase?
 MePedroCommunity AnswerPlayfair uses pairs of capital letters. If you want to have lower case letters too, the alphabet of the classic ciphers could be enhanced. All modern ciphers support all kind of characters.
MePedroCommunity AnswerPlayfair uses pairs of capital letters. If you want to have lower case letters too, the alphabet of the classic ciphers could be enhanced. All modern ciphers support all kind of characters. -
QuestionHow does W and L equal L? I didn't get that as my answer.
 Community AnswerIt's not W + L = L, but L + L = W. You take the written L, check with your keyword letter written under (L), and on your board you will find W.
Community AnswerIt's not W + L = L, but L + L = W. You take the written L, check with your keyword letter written under (L), and on your board you will find W. -
QuestionCan Vignere be used in combination with other ciphers (e.g. at-bash or a1z26)?
 Community AnswerYes, for instance: (your message), and if that was z gfxr cvd (not real message) you could just go: z=a, g=t, and so on.
Community AnswerYes, for instance: (your message), and if that was z gfxr cvd (not real message) you could just go: z=a, g=t, and so on.
Warnings
- This cipher is not fool-proof (no cipher is) and can be quickly cracked. By current standards, the Vigenère cipher is extremely weak. Do not use this for anything truly top-secret. For stronger encryption research AES and RSA. This cipher can, however, be used with a one-time pad as a key (a truly random sequence with the same length as the text that is only used once) to produce a ciphertext that, as long as the key is secure, cannot be cracked faster than just doing a brute-force attack.⧼thumbs_response⧽
References
- ↑ https://www.geeksforgeeks.org/vigenere-cipher/
- ↑ https://www.cs.uri.edu/cryptography/classicalvigenere.htm
- ↑ http://user.it.uu.se/~elenaf/Teaching/Krypto2003/vigenere.html
- ↑ https://pages.mtu.edu/~shene/NSF-4/Tutorial/VIG/Vig-Base.html
- ↑ https://pages.mtu.edu/~shene/NSF-4/Tutorial/VIG/Vig-Base.html
- ↑ https://pages.mtu.edu/~shene/NSF-4/Tutorial/VIG/Vig-Base.html
- ↑ https://pages.mtu.edu/~shene/NSF-4/Tutorial/VIG/Vig-Base.html
- ↑ https://www.boxentriq.com/code-breaking/vigenere-cipher