Similar to this question, Chrome is showing the connection cryptography as obsolete. Opera, IE and Firefox seem perfectly fine with the connection.
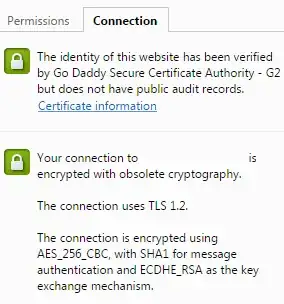
My guess would be the message authentication is using SHA1, but when I view the certificate information, the only mention of SHA1 is the Thumbprint. This appears normal for Windows systems. What exactly is 'message authentication' referring to and what do I need to change server-side to fix this?