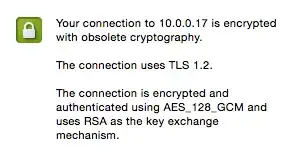
You can use openssl s_client -connect <server_name>:443 from linux to see the ssl handshake. Check the Peer signing digest, protocol, and cipher. Usally chrome has more details about the obselete configurations, you can try to update. Check if algorithm hash, ciphers, protocol are modern.
No client certificate CA names sent
Peer signing digest: SHA256
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 4499 bytes and written 415 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: <id>
Session-ID-ctx:
Master-Key: <key>
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
Start Time: 1579360646
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
Note: Openssl v 1.1.1 may fail to connect to server if the Peer signing digest: SHA1, you can try to reduce the security in /etc/ssl/openssl.cfn or /etc/pki/tls/openssl.cnf by setting the CipherString = DEFAULT@SECLEVEL = 1 and try again. With openssl you can set -ciphers -sigalgs and more to debug.