I'm trying to understand SSL/TLS. What follows are a description of a scenario and a few assumptions which I hope you can confirm or refute.
Question
How can my employer be a man-in-the-middle when I connect to Gmail? Can he at all?
That is: is it possible for the employer to unencrypt the connection between the browser on my work computer and the employer's web proxy server, read the data in plain text for instance for virus scans, re-encrypt the data and to send it to Google without me noticing it?
Browser on employee's computer <--> employer's web proxy server <--> Gmail server
The employer can install any self-signed certificate on the company computers. It's his infrastructure after all.
Scenario: what I am doing
- With a browser, open http://www.gmail.com (notice http, not https)
- I get redirected to the Google login page: https://accounts.google.com/ServiceLogin?service=mail&passive=true&rm=false&continue=https://mail.google.com/mail/&ss=1&scc=1<mpl=default<mplcache=2&emr=1
- I enter my username and password
- I get redirected to Gmail: https://mail.google.com/mail/u/0/?pli=1#inbox
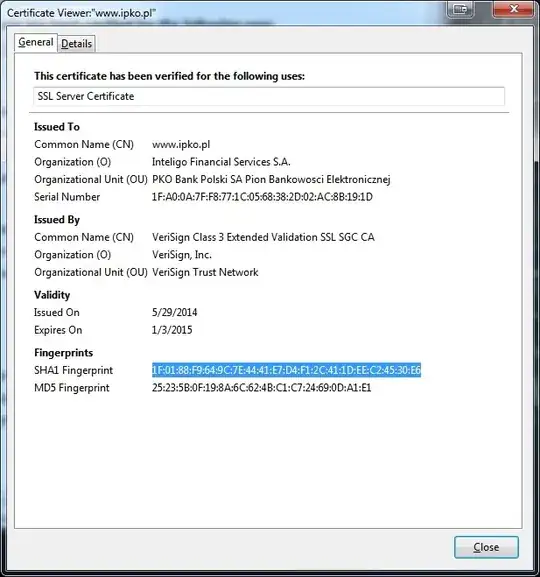
- I click on the SSL lock-icon in the browser...
...and see the following:
- Issued to: mail.google.com
- Issued by: "employer company name"
- Valid from: 01.01.2014 - 31.12.2014
- Certification path: "employer company name" --> "employer web proxy server name" --> mail.google.com
Assumption
I'm now assuming that the SSL lock-icon in the browser turns green, but in fact I don't have a secure connection from the browser to the Gmail server.
Is that correct?
Sources
I've read these sources but still don't quite understand it:
- Is there a method to detect an active man-in-the-middle?
- Preventing a spoofing man in the middle attack?
- How does SSL/TLS work?
Summary
- Is it possible for someone to be a man-in-the-middle if that someone controls the IT infrastructure? If so, how exactly?
- Is my login and password read in plain text on the employer's web proxy server?
- What should I check in the browser to verify that I have a secure connection from the browser all the way to the Gmail server?
EDIT, 18.07.2014
- Privacy is not a concern. I'm just curious about how TLS works in this particular scenario. What other means the employer has to intercept communication (keylogger etc.) are not relevant in this particular case.
- Legal matters aren't a concern. Employees are allowed to use company IT equipment for private communication within certain limits. On the other hand, the employer reserves the right to do monitoring without violating privacy.