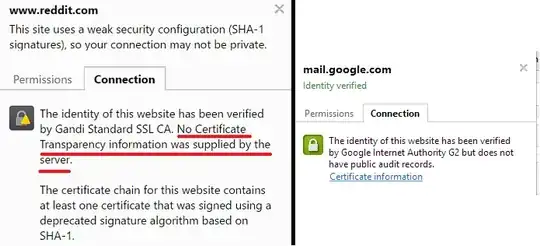
Note: If you're here because your certificate isn't trusted by Chrome, this is not the reason. Chrome will still trust certificates without CT information. If your certificate isn't trusted, there is an additional factor that you may have missed.
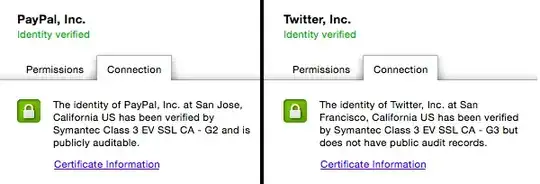
This has to do with the concept of Certificate Transparency.
The Problem
Browsers currently trust certificates if four conditions are met: (a) the certificate is signed by a trusted CA, (b) the current time is within the valid period of the certificate and signing certs (between the notBefore and notAfter times), (c) neither the certificate nor any signing certificate has been revoked, and finally, (d) the certificate matches the domain name of the desired URL.
But these rules leave the door open to abuse. A trusted CA can still issue certificates to people who shouldn't have them. This includes compromised CAs (like DigiNotar) and also CAs like Trustwave who issued at least one intermediate signing certificate for use in performing man-in-the-middle interception of SSL traffic. A curated history of CA failures can be found at CAcert's History of Risks & Threat Events to CAs and PKI.
A key problem here is that CAs issue these certificates in secret. You won't know that Trustwave or DigiNotar has issued a fraudulent certificate until you actually see the certificate, in which case you're probably the perpetrator's target, not someone who can actually do any real auditing. In order prevent abuse or mistakes, we need CAs to make the history of certificates they sign public.
The Solution
The way we deal with this is to create a log of issued certificates. This can be maintained by the issuer or it can be maintained by someone else. But the important point is that (a) the log can't be edited, you can only append new entries, and (b) the time that a certificate is added to the log is verified through proper timestamping. Everything is, of course, cryptographically assured to prevent tampering, and the public can watch the contents of the log looking to see if a certificate is issued for a domain they know it shouldn't have.
If your browser then sees a certificate that should be in the log but isn't, or that is in the log but something doesn't match (e.g. the wrong timestamp, etc), then the browser can take appropriate action.
What you're looking at in Chrome, then, is an indication as to whether a publicly audible log exists for the certificate you're looking at. If it does, Chrome can also check to see whether the appropriate log entry has been made and when.
How widely is it used?
Google maintains a list of "known logs" on their site. As of this writing, there are logs maintained by Google, Digicert, Izenpe, and Certly, each of which can maintain the audit trail for any number of CAs.
The Chrome team has indicated that EV certificates issued after 1 Jan 2015 must all have a public audit trail to be considered EV. And after the experience gained dealing with EV certificate audit logs has been applied, they'll continue the rollout to all certificate issuers.
How to check the logs
Google added a Certificate Transparency lookup form to their standard Transparency Report, which means you can now query for the domains you care about to see which certificates for those domains show up in the transparency logs. This allows you to see, for example, which certificates out there are currently valid for your domain, assuming the CAs cooperate.
Look for it here: https://www.google.com/transparencyreport/https/ct/
Remember that if you want to track a given domain name to be alerted when a certificate is updated, then you should follow the logs directly. This form is useful for doing point-in-time queries, not for generating alerts.