Why would you think that you can trust companies officially registered in some countries more than you can trust registered domains hosted in any?
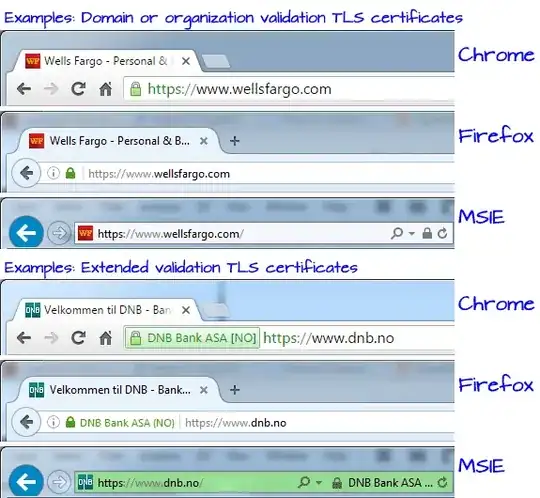
EV has obvious advantage with stricter validation, differences in trustworthiness between the other two however are rather moot. Browser vendors supporting EV simply didn't feel the need to agree on a separate visual identification of the other two (OV, DV) verification models, as neither provide a clear advantage one over the other (if any at all).
In short, none of the major browser vendors felt the need or want to differentiate between the two and stand behind it with their name. Good that they didn't, too. If companies can withstand scrutiny EV brings, then no one is stopping them to apply for such certificate. On the other hand, there are clearly also needs for cheaper certificates where additional verification wouldn't fit within their price range. Browser vendors (and user interfaces of some other software vendors) with EV support however don't stand by these cheaper certificates in any other special way than what is already there as per usual, for reasons mentioned before.
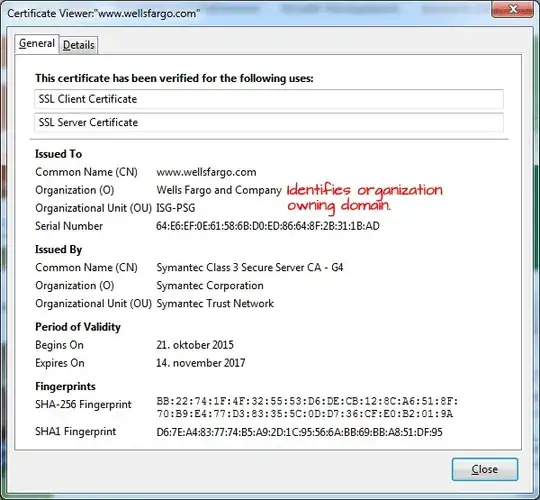
As for the other part of your question (visual inspection of certificate data), OV and DV would differ in their description where OV usually holds more data about the company it was issued for, but that's about it. This additional information display can vary across different clients, tho. That image you're attaching is however from Wikipedia, and you didn't mention what browser you were inspecting detailed certificate information in, so I can't say what differences you'd be able to see in an unknown browser.
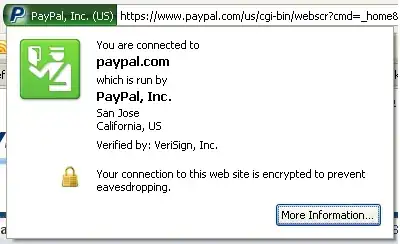
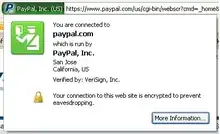
Example of Extended Validation certificate in Mozilla Firefox (above).
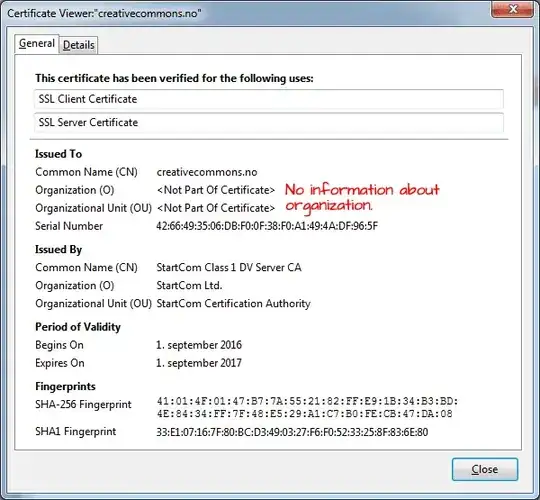
EDIT: DV certificate contains no identifying information in the organization name field. Typically, this value just re-states the domain name or simply says "Persona Not Validated", "(unknown)" et cetera. This is not standard for all CAs tho. Another way would be to inspect policy identifier (if present) where 2.23.140.1.2.1 stands for DV, and 2.23.140.1.2.2 for OV. Again, this is not adopted by all CAs. In short, there is no deterministic way to tell if a certificate was Domain or Organization Validated.
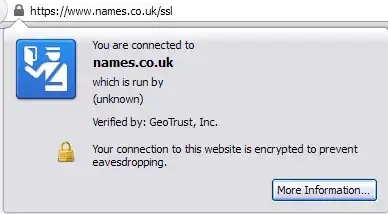
Example of Domain Validated certificate in Mozilla Firefox (above). Notice the lack of meaningful data in the organisation information field.