I have a trusted html file containing a script that handles sensitive information. When I open it in Chrome 108 on Android, it says:
What is this about?
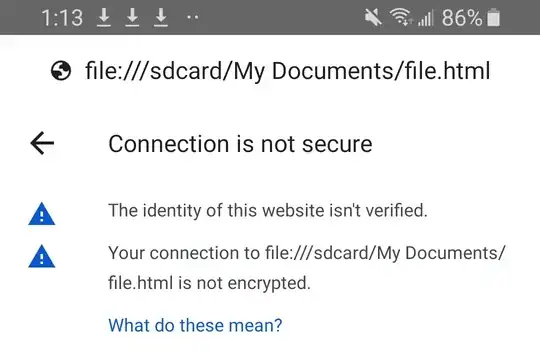
The above warning seems to appear independently of the method that file.html uses for communication. In fact, it appears even if file.html does not communicate at all! Clicking the "Details" link reveals the following:
This message seems to raise suspicion about the integrity of file.html itself. This is a file that I securely installed on my filesystem myself. Is Chrome saying that an attacker may have modified this file? How does Chrome let attackers modify local files in My Documents?
Or perhaps the message is in error? When I click on the "What do these mean?" link, Chrome seems to think I'm using plain http:// and not file://:
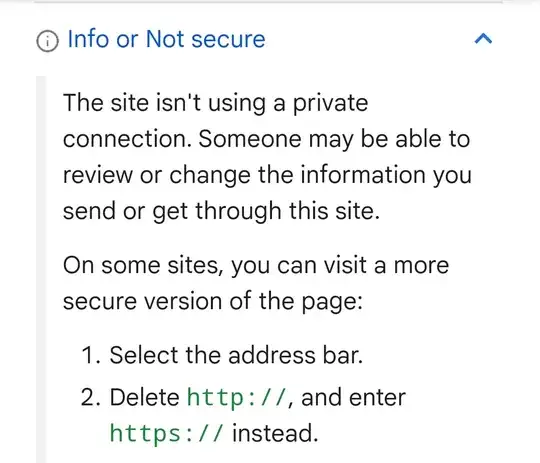
I am well aware that Chrome has issues with plain http:// (even on secure ports). But file:// is a different matter, as securing users' files is fundamental to system administration (assuming any software can be trusted at all). Local file access should be no less secure than any other method of obtaining a file from someone whom I am entrusting with my sensitive information. (In fact, local file access typically seems to be a necessary step in preparing delivery via other methods).
Of course, in some browsers, I also have to trust a script running under file:// not to read my local files. But then my files would already be stolen by the time I see this warning. Maybe Chrome is warning me not to enter local filenames? But that's not "passwords or credit cards", so Chrome's warning still doesn't seem to make sense.
Is there a logic to Chrome's warning about entering sensitive information into a page running as file://?