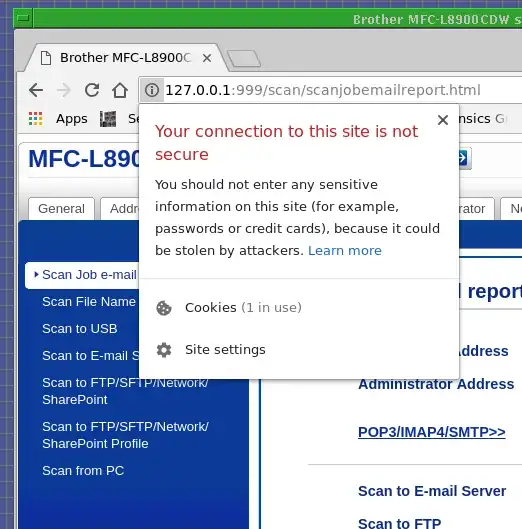
Please walk through how an attacker can intercept Chrome's connection to 127.0.0.1:999, as suggested by the warning below.
This warning is consitently displayed across many versions of Chrome in many OSes.
When I click the "learn more" link in the message, it says that SSL would be more secure, implying that an attacker can intercept Chrome's connection to 127.0.0.1:999. It is established that any user can open a port on 127.0.0.1. However, according to w3.org, only root can open port numbers below 1024. In light of this, how does the attacker pull off the interception in this case?