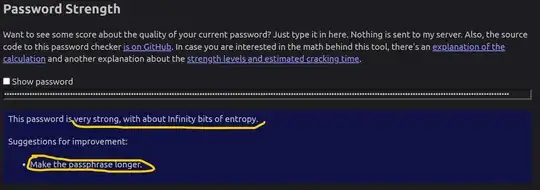
Is Rumkin.com's password tool a reliable tool for password strength checking?
I am asking because:
I am getting confusing suggestions:
D. W.'s comment to Jeff Atwood's answer claims that Rumpkin's estimates are apparently bogus.
Adam Katz's answer to my other question claims that password complexity detection tools are all wrong. So that would include Rumpkin's, try zxcvbn (that I've been using so far) and many / all others.
Please, note that this is not a broad question on whether all password strength checkers are unreliable. This has been addressed many times. But rather specifically about Rumkin.com's password tool. I want to learn whether this tool's suggestion system is flawed or if (in any scenario) a 777-character password may be considered not long enough (and therefore whether any system can or rather should suggest making it even longer)?