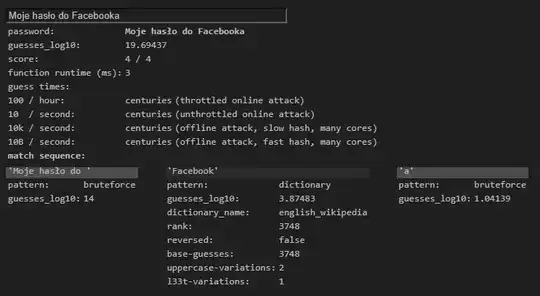
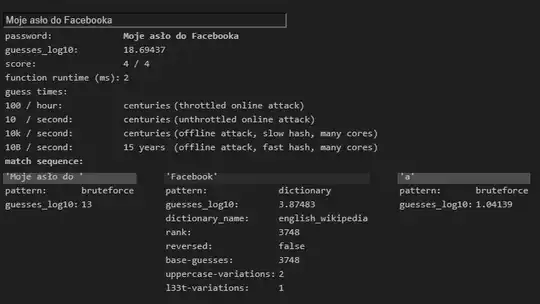
The password entropy calculation from this tool is not very accurate and is generating values I consider to be too high. That said, removing a character from a passcode will reduce its complexity by the number of iterations that character represents. Assuming the Polish alphabet's 32 letters (or 35 if including q, v, and x), your shorter password would make the password 32x (or 35x) easier to break, at least when missing the fact that this is a passphrase composed of words.
Password complexity detection tools are all wrong.
Password complexity cannot be calculated without knowing the formula used to create the password. Guessing that formula can be disastrous, as you have experienced with this tool.
Your Moje hasło do Facebooka password appears to use a formula of "four Polish words". This is not a good formula. When composing a passphrase, you must ensure that the words are randomly generated and not related to each other. "My password for Facebook" is a sensible sentence, so it is not a good password. (See also the infosec.SE analysis xkcd 936 for correct horse battery staple.)
If your password, quoted, might have hits in a Google search, it is not secure.
(This is an intellectual exercise; don't share potential passwords with a search engine.)
Let's instead assume your password was Poprawny koń zszywka bateria. The first thing you'll notice is that I translated each word separately rather than properly conjugating it as "Prawidłowa bateria zszywek dla koni". This is because the words must not be related to each other. In languages with grammatical gender, this might be a little confusing, but it's important because otherwise you're losing entropy. This is also why the English passphrase isn't "Correct horses staple batteries" or something else that's more of a sentence (the plural "horses" implies a plural for "batteries").
The complexity of this comes from the size of the dictionary. If you're using a standard English spelling dictionary, that's 100k. The Polish dictionary I just downloaded has 4000k, though that might be implausible; I just auto-generated a passphrase of ontologi trzebieszowskie niefortecznej nielitogeniczną, which seems like quite a mouthful.
There's a password-generation system called diceware, which has its own Polish diceware word list you could use. Example passphrase: plewka szpieg raban pruski ibi.
Diceware has a 7776-word dictionary, so a four-word diceware passphrase has an entropy of log₂(7776⁴) = 51.
This tool seems to ignore standard entropy measurement in bits truncated to an integer and instead measures in base 10, so log₁₀(7776⁴) = 15.56303.
Reducing a passphrase like plewka szpieg raban pruski ibi down to plewka zpieg raban pruski ibi actually increases its complexity since zpieg is not a word. In my own entropy calculations, I multiply words by six for typos/misspellings or iterations like l33t speak, so the entropy goes up by a little, from log₂(7776⁵) = 64 to log₂(7776⁵×6×5) = 69 assuming the attacker knows you've varied one word but not which one.
(Always assume attackers know your formula. Hopefully, they don't and will therefore take far longer to break your password, but calculating complexity needs to assume the worst-case scenario or else you're just hiding in presumed obscurity.)