The diagram below illustrates chaining digital certificates up to a publicly trusted Root Certificate:
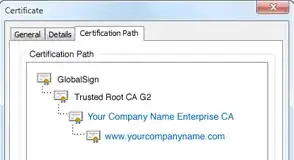
(source: globalsign.com)
I have been researching how trusted root authorities (such as GlobalSign or Verisign) are used to authenticate someone's public keys to identify that person as a trusted publisher. I think I am missing something, please let me know if I am misunderstanding something here.
So digitally signing involves hashing some data (message digest) with a trusted publisher's private key. Consumers of that data can use the trusted publisher's corresponding public key to verify the hashed data. Verifying the trusted publisher's public key (certificate) all the way up to a trusted root authority establishes the trust that the trusted publisher is who they say they are, correct?
In order for this chain of trust to work, I understand the importance of keeping private keys private. But I fail to see how this offers any trust or security on a compromised machine.
Say I am a malicious attacker who is trying to spoof a user on a machine I am already in control of. Like any good malware, I am going to want the user to think what they are doing is trusted. So it seems all I need to do is blow out any relevant valid certificates in the Trusted Root CA Windows Certificate Store and replace them with bogus self-signed certificates that appear to be valid. I could even re-create a chain of trusted certificates, such as in the image above.
This doesn't seem too far fetched to me yet. So, to complete the spoof, I would have to intercept the valid data and re-sign it with my bogus publisher certificate, "trusted" all the way to the "root CA". This seems far easier than stealing a publisher's private key.
EDIT: Is there a way to protect against such a targeted attack? For my very specific application, I need to know for sure that a cert is trusted, but that may not be possible on a compromised machine.