Though generally weak by constraint of human mental capabilities, knowledge-based authenticators have a unique property which the other two do not. That is, without technologically compromising the target client or server system (at which point n-factor authentication becomes fairly moot anyway), it requires a conscious effort on behalf of the owner for a knowledge factor to be disclosed to an attacker.
Your keys, ID badge, or other physical access tokens can be physically obtained by anyone within reach of them. This may take a moderate amount of effort on the attacker's part, especially to do it covertly. But, in the grand scheme of things, obtaining physical possession of most objects which are useful and convenient as access tokens is a fairly trivial matter.
Biometric data is even more trivial to come by. With today's technology, most convenient and affordable biometric authentication devices are still fairly easy to fool. And you're constantly spreading your authenticators everywhere on every surface you touch and in every photograph taken of you.
"Something you know", on the other hand, remains exclusively yours until such time as you personally choose to disclose it to a person or device. If you're properly storing a knowledge-based authenticator (that is, only in your head), it is nigh impossible for anyone to steal it against your will.
Nobody can simply snatch knowledge out of your purse, or lift it from a doorknob. They won't find it by combing through your Facebook pictures or rifling through your wallet when you're not looking. Your mind is yours alone, and it takes very extreme measures - especially compared to these - for anyone to take anything from it that you don't want them to.
Relevant XCKD:
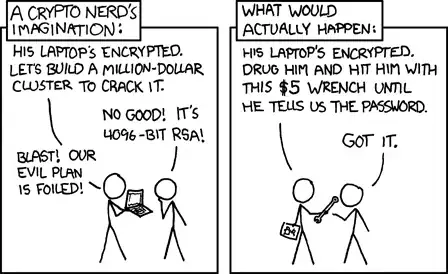
Playing it out a bit further:
2: Oh wait, we need his smart card!
1: Found it in his laptop bag.
2: And fingerprint?
1: Probably want to lift that before you break his fingers.
2: Okay, but I don't think he's gonna break.
1: Everybody breaks.
2: He says his name is "Jack Bauer".
1: Blast! Our evil plan is foiled!
