There are several lines of defense:
The obvious ones are to set BIOS password, (as you mention) use full disk encryption, do not use sleep mode, lock mode and especially not hibernation - encrypt it in CMD (Windows 7):
fsutil behavior set encryptpagingfile 1
Keep your important files in an encrypted container. A successfull cold boot might get into the FDE but not the container inside (correct me if I'm wrong)
Make sure you have DDR3 RAM, it has the lowest memory persistance for this attack, older types are a lot slower.
If you can, enable Power On Self Test (POST) in BIOS, it will attempt to zero out memory.
ECC memory will reset the memory during initialization. Check if you have it in CMD (W7):
wmic MEMORYCHIP get DataWidth,TotalWidth
If the TotalWidth value is larger than the DataWidth value you have ECC memory.
If you are physically hindered from shutting your PC down you may use remote shutdown software from smartphones. The ideal way is a an Android which binds the shutdown initation to a e.g. pressing up/down volume x times. This way you can shut down the PC with your hands in your pocket.
This is a golden nugget from a Blackhat paper. Unfortunately I don't have the slighest clue on how to implement this.
BIOS BOOT: Remnants of encryption keys can be recovered with very high probability, unless your master disk keys are stored in the physical address range 0x7c00– 0x7bff.
A disk encryption filter driver loads very early in the boot process and can allocate this memory range for its exclusive use.
512 bytes is enough room for multiple disk encryption keys, or for an AES 256 key schedule.
Any attempt to boot to ANY alternative operating system or device will overwrite the keys stored in this address range.
In the very same paper they discuss your question:

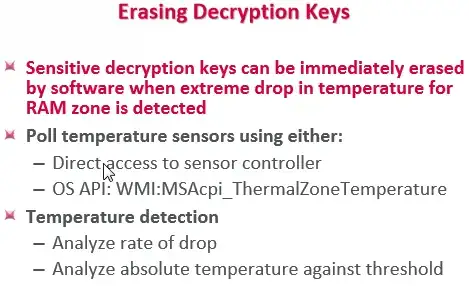
As for a software solution (I have not tested) but I can see that HWiNFO has an alert function, however I was not able to find RAM temp, but I didn't try very hard. 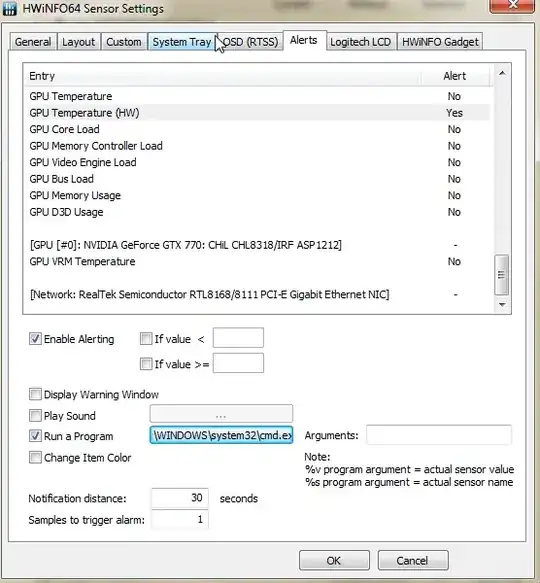
Lastly (something I have no experience with) you can "permanize" your hardware state by using Epoxy to make it difficult to remove hardware and/or difficult to introduce new hardware.
Sidenote: for those of you with a stationary PC, a chassis with screws and DDR3 memory is plenty of obstacles to prevent cooling of ram if you start shut down before attacker attempts anything.


