I'm new to the security stack exchange, so feel free to edit the question or redirect me to another forum if this is not fitting.
I'm currently working on a web application that will allow the user to manage their Exchange email account; read mail, send mail, create new folders, and so on. I want to support versions of Exchange as old as 2007, which only supports Basic and NTLM Authentication against their EWS API. This means that I have to store the user details in clear text, if only temporarily, on my server. The setup I have today looks as follows:
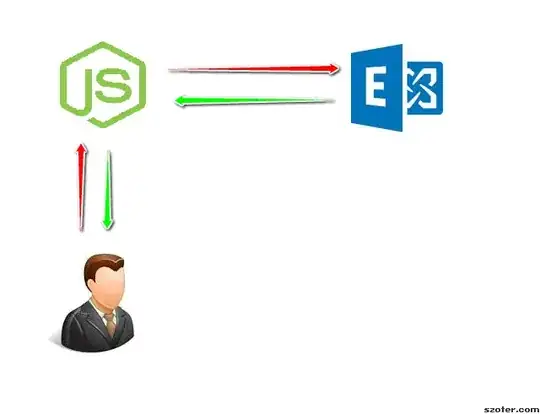
The user supplies their account information and EWS endpoint to my server.
This information is then checked to see if it is correct by issuing a simple GET-request to the endpoint, figuring out the "strongest" authentication method by looking at the contents of the "WWW-Authenticate" header. Authentication is done to see if the supplied username and password were correct.
If it was, I create a random token of length 32, and use it as key with the user credentials as value in a simple in-memory JavaScript Object, and return this token to the user.
The user is then able to fetch information, given that the token supplied in sebsequent requests' Authorization header is a valid one.
The sessions are deleted after one hour, and no data is ever persisted to a database.
I just found this great stack exchange a few days ago, and have been reading ferociously ever since (BASIC-Auth secure?, Are password stored in memory safe? to name a few greats). Security is not my forte, but I'm eager to learn, so please be harsh and tell me if I'm doing something reprehensible.
Is what I'm currently doing considered somewhat safe, or should I reconsider my approach entirely? Thank you.