If both your friend and his clients use gmail, then security is not that bad... all data transfers between a user's machine and gmail are over HTTPS, and if both sender and receiver use gmail, the email never leaves Google's machines. So, as long as you trust Google, that's fine.
"Trust" is a nasty word. In the paragraph above, it means that Google does not voluntarily discloses the email contents, and also that they do a good job of protecting their servers (you trust them to be honest, and you trust them to be competent). But, ultimately, someone you trust is someone who has the power to betray you.
Also, Google is known to scan gmail users' emails, so that it can work out targeted ads to display to the users. This implies, at least in a theoretical way, that data from your emails necessarily flows out of Gmail servers, towards advertisers. A comforting thought.
To get better than gmail, you need end-to-end encryption. The classic products are S/MIME and PGP; the former is supported by mainstream email applications directly, but involves X.509 certificates, which can be a hassle to setup. PGP usually requires add-ons, but tends to be simpler to use. Note that most webmails are incompatible with either S/MIME or PGP: Outlook Web App can do S/MIME with a specific ActiveX control on the client system -- Windows/IE only, of course -- but most other webmail systems cannot. To some extent, PGP emails can be handled externally by transferring them with copy&paste (the normal format for PGP emails is "ASCII-armor" which is meant to be transferrable as plain text).
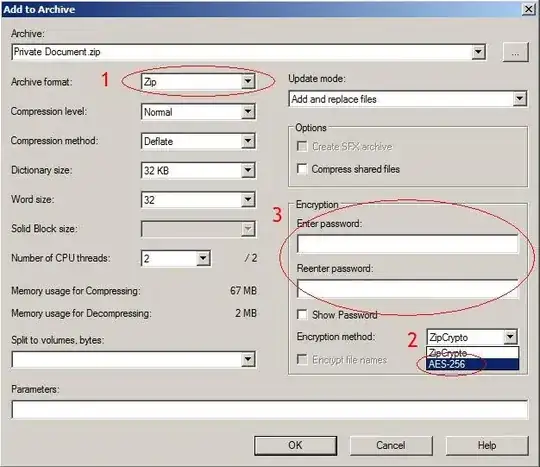
For one-shot communications, consider Zip archives with a password (password is exchanged over the phone). Older Zip implementations used a weak custom stream cipher (actually a good example of why homemade designs should be avoided). Newer Zip archivers (WinZip 9.0 and later, at least) use AES, which is much stronger. It all boils down to what the client is ready to install when asked by your friend.