I found a few posts which suggest using Microsoft SCM (Security Compliance Manager) to audit the security of Microsoft software solutions:
- Windows security policy analysis tool
- How do I apply a security baseline to Windows 2008 R2?
- IIS and SQLServer Hardening
Here's a sample screenshot of SCM, showing "261 unique settings" for Windows 7 SP1 computer security:
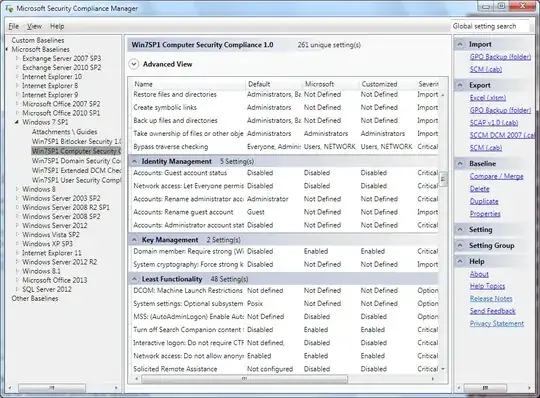
What I don't get is how these "unique settings" are audited. I mean, SCM seems to simply report all hardening options, rather than checking (auditing) whether they are applied to Windows.
So far, I found the following way to (automatically) audit the settings:
- Export them (using the panel to the right of SCM) as SCAP XML files.
- Use a tool such as OVAL or jOVAL to audit the system against the exported XML files.
Along the same lines, I use the following approach to apply a baseline:
- Export the baseline (or a customization thereof) as a GPO.
- Apply the GPO.
My question is:
Can SCM audit the settings itself, so that I don't have to export XML files and then use 3rd-party tools?