The image below shows how a packet is encrypted, and sent through the network.
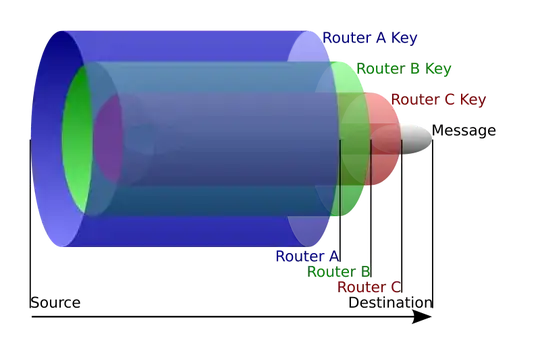
Tor uses its own protocol to negotiate encryption keys. Through this protocol the client receives encryption keys for Routers A, B and C.
From the Tor Project
The client negotiates a separate set of encryption keys for each hop
along the circuit to ensure that each hop can't trace these
connections as they pass through.
Before a packet is sent, it is encrypted with C's then B's then A's encryption key. When the message reaches router A it decrypts its layer, and forwards the rest to router B. Router A only know that the message needs to go to router B, and that it came from the client. It cannot see any other IP information.
For Tor (and onion routing) to work a minimum of 3 routers are required. So that no two routers will know both the source and destination IPs. When a Tor client sends a packet out the Entry Node will know the source IP address, but not the destination. The Exit Node will know the end destination, but not the real source address (just the previous relay). The IP address the server uses for the first layer will be the Exit Node's.
To address questions in your comments
If an Entry Node is compromised then it can reveal the source's IP address. But it will only know the next node in the circuit. Without some type of relationship to the destination the anonymity stays intact.
The Exit Node never seeds the original source address, and uses its own IP for communication with the end destination.
For more info look at the original Tor design paper.
