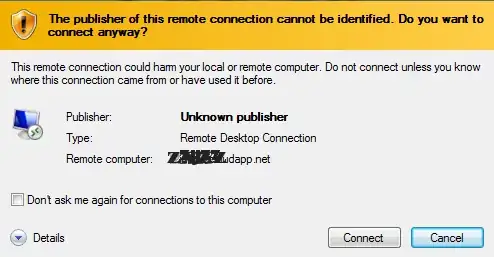
What security risks do you face when connecting to an (possibly foreign) RDP server? Opening an unsigned RDP file triggers the following warning:
RDP is a one way street, right?
What security risks do you face when connecting to an (possibly foreign) RDP server? Opening an unsigned RDP file triggers the following warning:

RDP is a one way street, right?
If the server's identity cannot be trusted, it is possible that you are subject to a man-in-the-middle attack. If that happens, an attacker can potentially read and/or alter your RDP traffic in either or both directions.
Having a MitM on RDP is just as bad as dealing with one on a web session, if not worse. Anything you send to the remote system - keystrokes, mouse activity, file/clipboard transfers, etc. - can be monitored and recorded by the attacker. Additionally, the same can also be altered by the attacker. Traffic coming to you is just as vulnerable. The attacker can see and hear all of the output from the remote system, as well as possibly alter it in transit. They could use this to inject malicious payloads into file/clipboard downloads or take over the session. Any local resources you share (e.g.: printers, local/networked drives, etc.) are put at risk as well.
That being said, most of these warnings are probably benign. The most common reason for seeing this is because the system is using a self-signed SSL certificate instead of one from a trusted Certificate Authority. This is the default configuration for all Windows systems, and usually is not changed except in very security-conscious business environments.
If you want to be sure whether you can trust a self-signed certificate, you need to check the certificate on the system locally first. Note the certificate's fingerprint while logged in locally, then compare it to the fingerprint of the certificate presented over RDP when you try to connect.