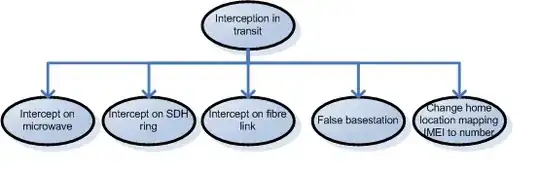
My current understanding is that sniffing traffic on 4G (lets use Wimax and LTE for the purposes of this question) and 3G is not a simple matter and either requires you setting up a fake base station that people connect to or having insider access to the Carrier (physical or logical)
Here is an article today on Defcon 4G hacking. It does involve installation of an update on Android: http://seclists.org/fulldisclosure/2011/Aug/76
How difficult is this to do? Can someone elaborate the attack tree in a relatively abstract or way that is easy for a non mobile technical person to follow?
Question also sparked by the fact I couldn't find a definite source to say the Facebook iPhone and Android apps use TLS.
My current understanding: