According to process of authenticating a server certificate:
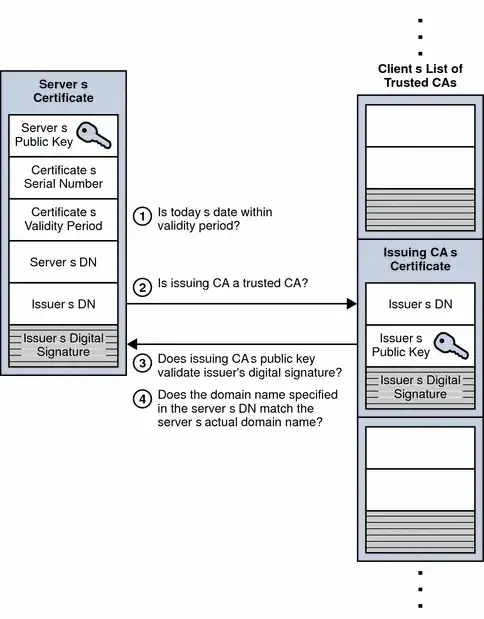
What's keeping a malicious server to fill up a valid server certificate since it knows all the things:
- Forged Server public key (man in the middle public key instead of actual server public key)
- Certificate serial number. (actual server)
- certificate validity period (actual server)
- Server's DN (actual server ... but we are sitting in the middle of the IP route)
- Isser's DN
- Issuer's Digital Signaure
This question is similar to (How does an SSL server prove its identity?) which deals with step 4, but I am interested in step 3