I was about to reset my Facebook password and got this error:
Your new password is too similar to your current password. Please try another password.
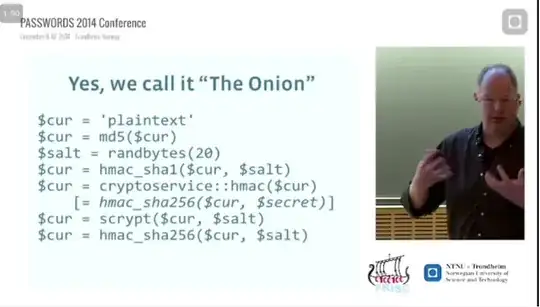
I assumed that Facebook stores only password hashes, but if so, how can they measure passwords similarity? This should be impossible with good hashing function, right?
Question is - how is this possible and what are the implications?
Thanks in advance.
UPDATE
I didn't make it clear - I was not asked to provide old and new password. It was the "reset password" procedure, where I only provide a new password, so most of answers of suggested duplicate are not applicable.
UPDATE2
mystery solved - see comment (from Facebook engineer)