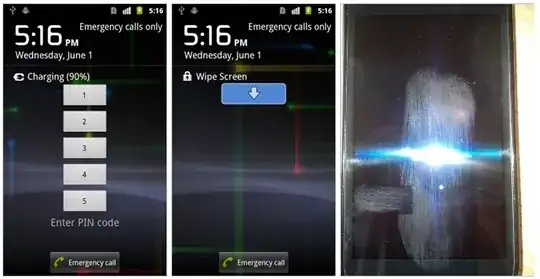
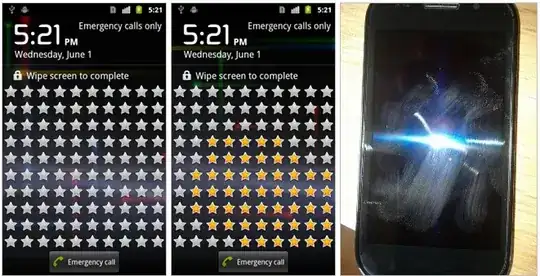
This is known as a 'Smudge Attack'
It really depends on how much you've used your phone since you've last unlocked it, but the general principle still stands. If you use the pattern feature of Android phones, this can be particularly obvious.
The University of Pennsylvania published a research paper on the topic and basically concluded that they could figure out the password over 90 percent of the time.
The study also found that “pattern smudges,” which build up from writing the same password numerous times, are particularly recognizable.
Furthermore:
“We showed that in many situations full or partial pattern recovery is
possible, even with smudge ‘noise’ from simulated application usage or
distortion caused by incidental clothing contact,”
While this is a plausible risk, It is not a particularly practical vulnerability as an attacker needs physical access to your phone. Using a PIN Code over a pattern may reduce the chance of this presenting a threat but it still exists depending on the strength of your PIN and the cleanliness of your hands/screen. However, these same researchers postulate another possible attack using the heat residue left by contact between your fingers and the screen which would be another problem altogether.
Obviously, cleaning your screen after every use is a practical (and not too difficult) defense against this specific attack. I'd expect that if you have used your phone (say to make calls/send a message/any kind of web browsing) it would also sufficiently obfuscate the patterns/codes. From examining my screen this seems to be the case.