My university provided me with the following slide which is confusing me:
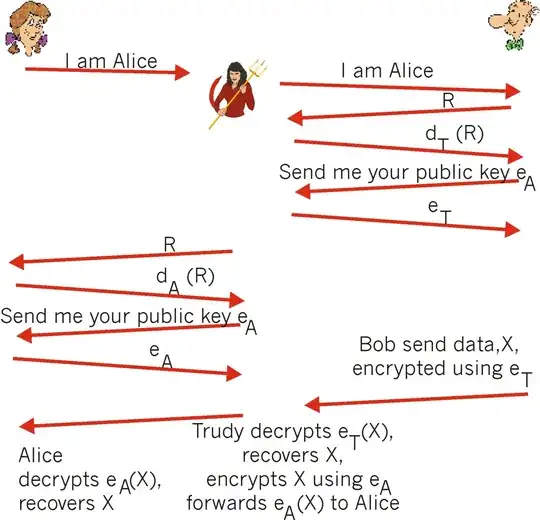
From my understanding, what is happening here is that Trudy (Person in the middle) is pretending to be Alice. Bob then authenticates Trudy as Alice. Other than that however I'm really able to explain what else is going on here.
Also, can this happen in symmetric key cryptography? The way I understand it, this can happen because as Alice and Bob exchange keys, Trudy could take it if the security was not good enough and then use it to pretend to send messages in place of Alice.