I am behind an HTTP proxy, and I frequently tunnel out via an ssh -D SOCKS proxy (I have access to a couple of outside servers which I can tunnel to) when the HTTP proxy causes problems1.
Now, this works for me, but I have some friends who need a SOCKS proxy for similar purposes. I can't give them my SSH access, for reasons beyond my control. The only alternative I can think of (besides those china tunneling sites) is Tor because it sets up a SOCKS5 proxy on port 9150.
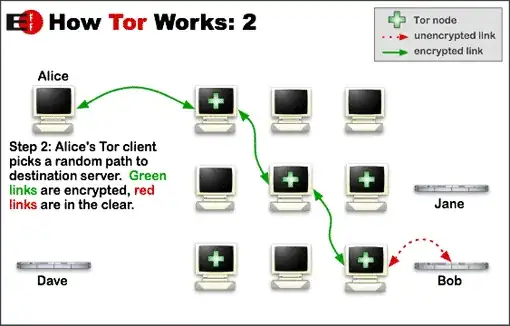
However, I'm not sure how safe Tor is from snooping and other MITM attacks. I don't care about the anonymity provided by tor — we're using it for the purpose of having a tunnel, not for anonymity.
However, I wonder how secure it is to use Tor for normal traffic. Cookies/login information probably could be stolen by a snooper, and there could be other types of MITM attacks as well. I don't understand Tor well enough to figure this out myself.
How safe is Tor from these attacks? Is there any way (connecting to a trusted node/etc) to create a relatively safe Tor proxy?
1. For example, the HTTP proxy eats WebSocket connections, while the SOCKS proxy lets them through unmolested.