Yes, it is a threat. Not just with open networks, any network owned by someone you don't trust (like mall networks which are secured but provide a password) There are many things they can do:
Read all your unencrypted traffic
Anything you send over an http connection can be read by them. Passwords, usernames, credit card numbers, the works. All of these are sent in plaintext and can be easily logged.
Many apps run on unencrypted connections as well. There's a lot of important information that can be snooped from those.
Phish all your encrypted traffic
Usually it's hard to spoof HTTPS because you need a valid certificate for that to work. However, many times you type in an HTTP URL in the address bar and it redirects you to the HTTPS equivalent. For example, when you type http://mail.google.com in the address bar, you get the following (it's a redirect):
<html>
<head>
<meta http-equiv="Refresh" content="0;URL=http://mail.google.com/mail/"/>
</head>
<body>
<script type="text/javascript" language="javascript">
<!--
location.replace("http://mail.google.com/mail/")
-->
</script>
</body>
What if this wasn't there? While apps which directly access GMail will still work (they know about https), anything you type in the address bar that is not explicitly https can be phished. They can redirect you to a fake GMail, where you will log in and they will steal your credentials. While two-factor authentication helps, it does not prevent them from stealing your cookies, which will give them access to your account until you log out.
The reverse is also possible. They can use a 301 Moved Permanently redirect to serve you HTTP when you ask for HTTPS, and they'll give you something which says http://mail.google.com in the URL but really points to a completely different server. Both mobile and desktop browsers seem to allow 301 redirects without a fuss.Desktop browsers make a fuss when there's an unauthorized HTTPS redirect, but mobile browsers don't.
On modern desktop browsers, it is easy to identify when this is happening, for example, Chrome shows this:
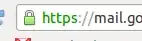
when on an https connection. If you are alert, you'll notice if the HTTPS is replaced with HTTP on a desktop browser(since the icon is no longer green), but most mobile browsers don't seem to have any way of indicating a secure connection.
This problem can be solved (on the site side) by using HSTS, and on your side by using bookmarks and keeping browser history.
Unauthorized access to device
Depending on your sharing settings (and what you set the network as -- always, always use "Public" for networks you don't trust), it may be possible to access your Windows filesystem. Unless you have ssh or telnet set up (and if you do, I assume you know how to keep it secure), Linux is generally safe from this. Most phones are as well.
