Consider the picture below (taken from page 21 here). Is this possible? If so, how can I prevent it?
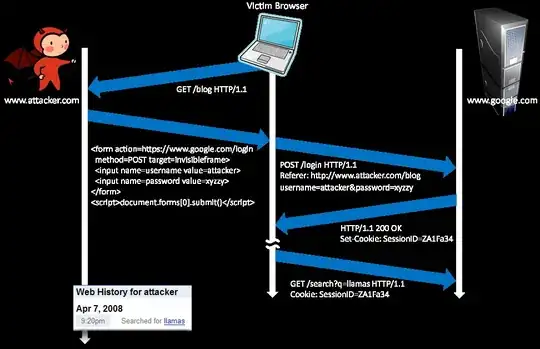
Consider the picture below (taken from page 21 here). Is this possible? If so, how can I prevent it?

Yes, it's possible. Or rather, it would be possible, except that Google has deployed countermeasures to defend against precisely this attack.
This attack is known as "login CSRF". It's similar to a standard CSRF attack, but a little different. If you search on "login CSRF", you will find information on the attack. It is a real threat against some web services. For more details, see my answer to a related question, and the following research paper:
See especially Sections 1-3 of that research paper for more technical details. The paper describes how to defend against the attack.
The short version of how to defend against the attack is that you include a secret CSRF token in all POST requests, including login attempts; and on the server side, you require that login attempts have the proper secret CSRF token included. OWASP has more on how to deploy secret CSRF tokens.
The goal of a CSRF attack isn't usually to steal credentials, or to log in though stolen details, but to get a valid account to perform an action chosen by the attacker. For example, if an administrator of a target site were victim of an CSRF attack, they may elevate a non-admin account to an admin account without realizing it.
This can either happen through an XSS flaw on the target site itself, or the administrator could be tricked into visiting a malicious website that executes a command against the target site (as shown in the image above). Or the administrator could have been tricked into visiting their own site directly, for example: http://somesite.com/edit_user.php?action=setClass&class=admin&userId=23443 (not sure if this counts as CSRF still, or if it's just social engineering).
To protect against this you can use CAPTCHAS on pages that perform important actions, or you can use secret hash codes to attempt to verify that a request is wanted.
There's a good description and suggestions for countermeasures here: https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)