I generated the public and private key with
openssl req -x509 -nodes -days 365 -newkey rsa:4096 -keyout server_key.pem -out cert.pem
and I am using c sockets for the server and client with openssl, every thing works fine and I can capture the encrypted traffic using
sudo tcpdump -w - -U -i eth0 -v 'port 1337' | tee packets | tcpdump -r -
serverIP: 10.10.0.6
clientIP: 10.10.0.12
My question is: how do you decrypt the traffic in Wireshark with/without using the private key because it does not seem to be working?
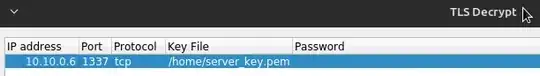
I have tried to add the private key: 'Edit'->'Preferences'->'Protocols'->'TLS' then added the server_key.pem to the RSA key list with 10.0.0.6 for the ip 1337 for the port and tcp as the protocol but I still can't decrypt the packet with the application data.