Don't be “clever”. An obscure reference you come up with could be less obscure than you think. For example, your offered passphrase is a quote from JRR Tolkien's The Fellowship of the Ring and is therefore not strong enough (a persistent and well-informed attacker will crack that in days at the longest). Don't hide behind perceived obscurity; passphrases are just like passcodes: they need to be random. You wouldn't have a passcode of abcdef123 or 1qaz2wsx (look at a qwerty keyboard), would you?
If a Google query for your password (quoted & de-0bfuscated) might get hits, it is weak.
(This does not mean that a lack of Google hits denotes a strong password.)
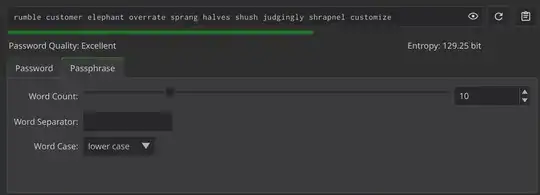
Use a password generator. Many pw generators have an option for pass phrases. For example, I just opened Bitwarden and generated nerd-shifting-porous-naming-dictation as a password.
Password managers remove the need for memorable passwords. Assuming a dictionary size of 100k words, a five-word passphrase has an entropy of log₂(100,000⁵) = 83. That's pretty good, but for 37 characters of fully random ASCII printable characters, log₂(94³⁷) = 242. You might as well go with the stronger one.
Passphrases don't satisfy complexity requirements most of the time. Most passphrases don't contain the necessary capital letter, number, and symbol. Password generators ensure there's at least one of each of those when they make a code but not when they make a phrase.
Maximum password lengths are incompatible with passphrases. Also be aware that some systems have an unreasonably short length limit on passwords—for no valid reason (I understand limits like 128 characters, I am stymied by limits like 12). If you're limited to even 20 characters, a passphrase won't provide much security.