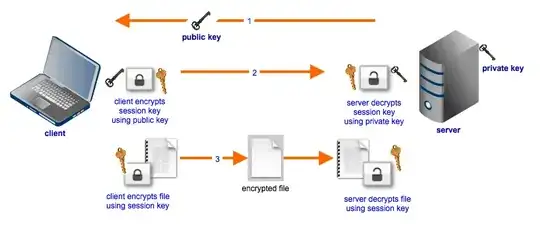
(shown in step 1): Is the initial process in public key encryption where the public key is transferred across the network done in plaintext? It seems like it must be, which essentially means that no matter if a victim is using HTTPS or a VPN on a public network, if the initial process is done in plain text, than a middleman who has full access to the network traffic can essentially just intercept that initial public key transfer process, steal the key, and effectively intercept the rest of the victims "secure" transmission in their "secure" internet session?
So if I am right, public networks are only secure as long as the device obtaining the public key was there before the attacker was?