You are incorrect in saying BitLocker without a TPM is less secure, as the underlying encryption key is the same in all cases. How you balance protection and convenience in accessing, protecting, and providing backup archives of protectors of that key is what determines your level of security.
You are correct that once the machine is running it is vulnerable to many forms of attack, however this is true of all encryption tools regardless of vendor. The running system must have the encryption key available in order to operate, and a sufficiently motivated hacker can extract the key from the system while it is operating.
With a TPM a startup key is stored within the TPM, which for convenience will provide the key to the secure bootup sequence. It is possible for the TPM to be damaged or otherwise lose the key, requiring the recovery key to be entered manually from an archived copy (paper, stored in Active Directory, store in your cloud account, stored in a file on another drive, etc.). It is only as secure as your archived keys. If you choose not to archive the key the drive will be unrecoverable.
With a TPM and PIN the startup key is stored within the TPM, and is protected by the PIN. If the PIN is entered incorrectly too many times the TPM will lock which prevents the startup key from being accessed even with a valid PIN. The key must be entered manually from an archived copy as above, and the TPM reset to resume using the TPM or TPM and PIN options. This is more secure than option 1, however it is only as secure as your PIN and archived keys. If you choose not to archive the key and forget your PIN the drive will be unrecoverable.
Without a TPM the key can be stored on the drive and protected by a password. The password is protected, however it is technically vulnerable as there is no separation between the password, key, and data. There is no lock available to lock the password as the hard drive can be duplicated and restored to any previous state. While this is at least theoretically not secure, realistically it is as secure as your chosen password and the encryption algorithms Microsoft has used to protect the password and key on the disk. If you choose not to archive the key and forget your password the drive is realistically not recoverable.
Without a TPM a startup key can be stored on a USB drive. The computer and hard drive have no copy of the startup key, so you are required to provide it by inserting the USB drive during the boot up sequence. Once the system has booted the USB drive can be removed and left on top of the computer, or preferably placed in the secret vault under your bed at your secret lair known only unto yourself. This can be more secure than option 1, 2, or 3 however it is only as secure as your USB drive and archived keys. If you choose not to archive the key and lose the USB drive containing the startup key or it becomes damaged it will be unrecoverable.
- In all cases I assume no key loggers or other hardware level or software level compromises exist such that you or Microsoft give your PIN, password, or keys away. If you need security at a Faraday cage level BitLocker won't save you. There have been security issues that have previously impacted BitLocker and other full disk systems. There are security issues that currently impact BitLocker and other full disk systems.
To enable options 1-4 open "Edit group policy" and navigate to Local Computer Policy->Computer Configuration->Administrative Templates->Windows Components->BitLocker Drive Encryption->Operating System Drives->Require additional authentication on startup. Configure it as Enabled, and set the remaining options as needed for your preference. Generally 'Enabled' is sufficient, as the remaining options default to "Allow" rather than "Require" or "Do not allow". Other useful policies are available here including "Allow enhanced PINs for startup", PIN length, password length, permitted algorithms, required algorithms, etc..
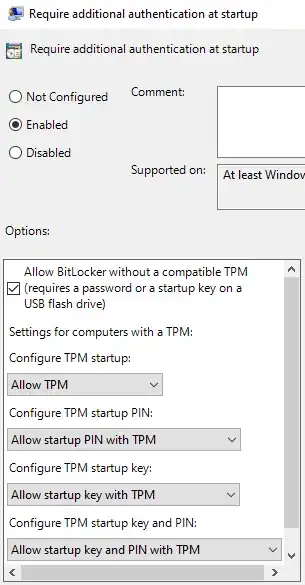
Once you have enabled your policy choices, Manage BitLocker will present additional options.
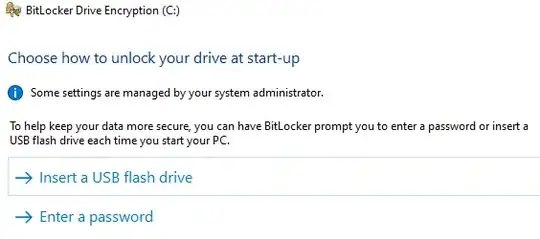
If you wish to go further additional options are available including TPM and USB drive, TPM and USB Drive and PIN, Certificate, network unlock, etc.. These can be researched by running the command lines "manage-bde -on -?" and "manage-bde -protectors -add /?". I won't include them here as I believe option 2 using TPM and PIN is sufficient for what you are looking for.
- Without a TPM you can memorize the recovery key. It is as secure as your threshold to extraction by torture or guile, and the note scribbled under the keyboard as your archived copy. If you forget your key it is unrecoverable. Notwithstanding future technology or defects in the algorithm the 50 digit recovery key will take a billion computers running a million attempts per second many many times longer than the age of the universe to crack the recovery key.
To enable option 5 configure the policy as above, and configure BitLocker to use a password. When prompted to backup the recovery key select to print it, select the Microsoft Print to PDF option, and save the resulting PDF to the protected drive. Open the PDF and memorize the recovery key. BitLocker will need the machine to be restarted. After the machine is restarted and BitLocker is fully enabled you may delete the PDF. The intention is simply to destroy all archives of the recovery key, so any method you choose will be somewhat secure. Save it to a USB drive and grind the USB drive, print it to paper and burn it, etc. but make sure the only copy is in your head. Now use the command line to run the command "manage-bde -protectors -delete c: -type password" and reboot the system. Windows will now prompt you to manually enter the recovery key at every boot.

