The BIOS module stores the CRTM (Core Root of Trust for Measurements) and as per TCG specification it should be immutable. CRTM measures the integrity of rest of BIOS code. CRTM ensures that measurement taken is valid and then give control to rest of BIOS code.
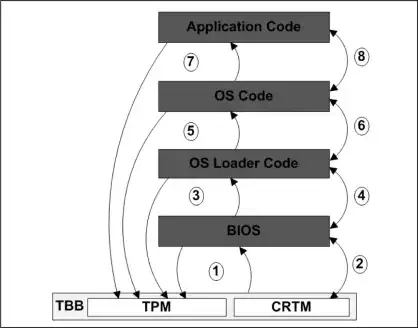
This measurement also involves Digital Signature verification, and public keys for verification are hardwired AFAIK (also known as Hardware root of trust). The BIOS code is generally digitally signed. So, if you modify the BIOS code, the signature verification will fail and CRTM won't pass the control to the rest of BIOS code.
Below link will be helpful:
root-of-trust
