I was reading an article which said that if you install custom root
cert from a third party then they can decipher all communication
between you and others.
Its common practice for organisations to use internal certificate authorities to decrypt traffic as most internet communication is encrypted now. Although it's theoretically possible to decypher all traffic send and received by you, in practice storing this information would require a huge amount of storage. Usually, packets are inspected using the CA for SSL decryption then if the packet is allowed to pass through the firewall, the decrypted traffic is discarded.
The image below demonstrates the process well:
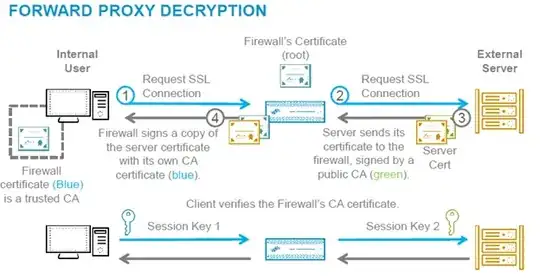
Without using the internal root CA the companies firewall, IDS/IPS, etc., can only scan a packet's headers to determine if it should be permitted or blocked.
With SSL decryption, the firewall decrypts the entire packet to scan its full contents, known as DPI (Deep Packet Inspection). DPI allows for better protection from malware and can also be used to detect applications that should be blocked using non-standard ports to bypass firewall rules, for example, FTP using port 80 vs 21.
So unless someone(company, work, hacker, etc) really tries to
impersonate by doing mitm. Only then the compromised root cert will
come in play as that would be used to pass fake cert as valid cert.
That's correct; the process of SSL decryption is a MITM attack.
otherwise just simply having a custom root cert isn't like decrypting
all your ssl traffic. Unless the same org has also installed a
software that acts as a proxy for all internet traffic. It requires
active intercepting, decrypting, and re-encryption of all traffic. So
either by installing malware on the computer or monitoring internet
traffic.
That's also correct; the certificate alone is just a certificate that's trusted within your machine. The organisation will need to pass your traffic through them somehow to perform the MITM. This is usually through a VPN, proxy or by default if you're connected to the internal network.
If you wish to learn more about how SSL decryption works the following white-paper is good: https://www.paloaltonetworks.com/apps/pan/public/downloadResource?pagePath=/content/pan/en_US/resources/whitepapers/decryption-why-where-and-how
