Sometimes I have to fix an infected WordPress website. I always check the infected website from a virtual machine (Oracle VM VirtualBox). I'm also running Norton 360 DeluXe on the host machine.
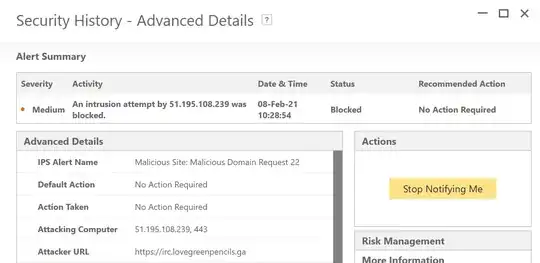
In the 2 most recent projects, for both, I received a notice from Norton that 'an intrusion attempt was detected and blocked', on the HOST machine. So apparently the malware can 'breakout' a VM? (Despite having read this article, that it should be totally isolated.)
As how can Norton otherwise detect this as the page was opened in the VM?
Also Norton says: No action required, is that really true? Could the host be infected with stuff Norton did not detect?
It does not feel safe anymore to use a VM to visit infected website. Should i be worried? Did i do anything wrong? What are the alternatives?