First of all, let's have a look at how a Man-in-the-Middle attack works.
Instead of Alice connecting directly to Bob, Alice instead connects with Eve (who claims to be Bob) and Eve connects with Bob while pretending to be Alice.
This means that MitM attacks are active attacks, and not passive ones. An attacker cannot simply copy traffic passively and decrypt it there - they need to actively interfere with the connection.
About your Employer's Case
Here, "interfering" with the connection is basically equivalent with "providing" the connection. As such, when you use your employer's network, you can assume that your connection goes through a proxy, who will do some sort of inspection of the traffic and possibly block certain domains.
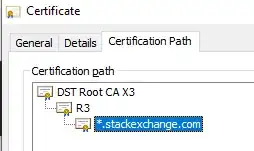
As for TLS interception, in order to do that, an employer needs a root certificate that your machine considers trustworthy, and act as a TLS proxy for the network. The easiest way to see if this was done is to check the certificate chain of a website you visit and compare that with the certificate chain from a connection you trust to not be intercepted.
On an intercepted connection, the root certificate will be the one your employer installed, whereas on the unintercepted connection, the root certificate will be a public CA.
What can you do about this?
Nothing. Plain and simple - nothing. You could delete the root certificate from your computer's trust store, but that will just result in error messages from your browser. If you choose to ignore the error messages and still proceed, your connection will be intercepted just like before - with the added downside that others can now also intercept your traffic and you wouldn't be able to tell.
So if you want to use the web without your employer knowing what you do, use a private device with a dedicated connection (e.g. your phone and mobile data) - do not connect this to any corporate device, I guarantee you that a slap on the wrist from the IT department is the best outcome in all of this.