Note: I've already read Is it ok to send plain-text password over HTTPS? and https security - should password be hashed server-side or client-side?, but here it's about a specific replacement method (see below).
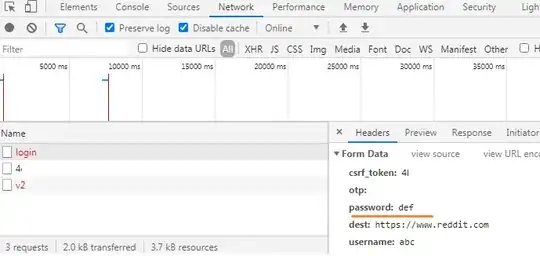
After reading an article about a new authentication method on the Cloudflare blog, I looked at the POST requests that are sent while authenticating with "Developer Tools > Network". Many popular websites (Reddit, HN, etc.) still send the password in plaintext in the (SSL-secured) POST request (see screenshot below).
Is this login method still industry standard?
Is the following alternative more secure than sending plaintext password over HTTPS?
signup: client generates a random
salt, and sends the tuple(username, salt, hash(plain_password + salt))via aPOSTrequest. Then the plaintext password never reaches the server.subsequent logins: the server has to send
saltback to any client who tries to login with a givenusername, so that the client can hash with the same salt. So this means that the server is disclosingsaltto anyone trying to log in with a given username.benefit: the server stores a salted+hashed password (which is standard) but also the server has never, ever, seen the plaintext password even once (so if the server is compromised, the risk is limited)
Notes:
since
H = hash(plain_password + salt)now behaves a little bit like a newplaintext(see the 2nd answer of Zero Knowledge Password Proof: why is hashing the password on the client side not a ZKP?), then the sever can store(username, salt, server_salt, hash(H + server_salt))in the database, instead of(username, salt, H).to mitigate risks for replay attacks, the server can also send a unique
nonce, along withsaltfor each login, that expires after one login attemptthe main goal here is that the server never ever has access to the plaintext password or a simple hash of it (that could be often reversed with a single rainbow table for the whole site). I'm ok with the risk that an attacker has to compute one rainbow table per user.
Example attack I'd like to mitigate: if the server has access to a plaintext password and it is compromised (example Spectre / Meltdown vuln.) then the user's plaintext password (possibly reused on other websites) could be stolen, before it is salted-hashed and saved to the database.