I manage an Ubuntu server that runs a number of WordPress sites. This morning one of them went down and was showing the exception
PHP Fatal error: Namespace declaration statement has to be the very first statement or after any declare call in the script in /var/www/vhosts/new.wearesno.com/httpdocs/wp-content/plugins/w3-total-cache/Cache_File_Generic.php
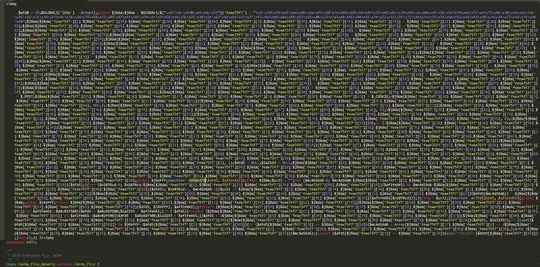
I went and had a look in that file using nano in the terminal and it looked normal - with the namespace declaration straight after the opening <?php tag. However, when I downloaded the file to my Windows PC I could see that it contained this:
I then went and downloaded a backup of all the sites on the server and did a search for $GLOBALS;$ and found a large number of files containing similar content at the top of the file.
Presumably this is a shell of some sort that will allow an attacker remote access to the server. Does anybody recognise specifically what it is?
I'm hoping that because the sites are behind CloudFlare that the attacker doesn't know the actual IP address of the origin server and so if they are opening a socket on the server, the attacker doesn't know the IP to connect but I'm not 100% sure on this.
Open to any suggestions on how to best secure the server.