Our system supports SAML2 and acts as service provider. Our customer uses ADFS as identity provider. Metadata has been exchanged and the connection works. Unfortunately our system complains about the SAML responses:
org.opensaml.common.SAMLException: NameID element must be present as part of the Subject in the Response message, please enable it in the IDP configuration
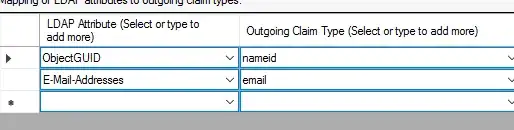
We confirmed that our customer has configured NameID as outgoing claim in their ADFS:
To provide further assistance to our customer we want to look at the Assertion in the SAML response to take a look at the problem's cause. Unfortunately the application logs the SAML response containing the EncryptedAssertion and I am unable to decrypt it locally.
I was able to decrypt a SAML response from a development stack I ran locally via samltool.com but the page recommends not to upload production keys. I checked with IT and they told me to figure out how to decrypt the EncryptedAssertion using the private key via openssl or a custom Python script.
So far I tried openssl rsautl:
$ cat encrypted_assertion.txt
6MFicPXJ3ycJtj3grCsaY4zxk2eEXQ3s2eCXGDCtJMMKN4PcgCCihA/jljs2jbfo/bC+xegsU74u
-- snip --
gX+ZooI5tUSkJLrpiQ==
$ cat key.pem
-----BEGIN PRIVATE KEY-----
MIIJQgIBADANBgkqhkiG9w0BAQEFAASCCSwwggkoAgEAAoICAQCoLiGwr/Y1vKPq
-- snip --
ldEZugZ5D51b1d63LkM9UvCyGLFrQA==
-----END PRIVATE KEY-----
$ cat encrypted_assertion.txt | base64 -d > encrypted_assertion.bin
$ openssl rsautl -decrypt -in encrypted_assertion.bin -out plaintext -inkey key.pem
RSA operation error
4499476076:error:04FFF06C:rsa routines:CRYPTO_internal:data greater than mod len:/AppleInternal/BuildRoot/Library/Caches/com.apple.xbs/Sources/libressl/libressl-47.100.4/libressl-2.8/crypto/rsa/rsa_eay.c:503:
and openssl enc to no avail (the content of cdata.bin is binary):
$ dd if=encrypted_assertion.bin of=iv.bin bs=16 count=1
1+0 records in
1+0 records out
16 bytes transferred in 0.000436 secs (36692 bytes/sec)
$ ivhex=$(od -t x1 iv.bin | sed 's/^[0-9A-Fa-f]*//' | sed 's/ //g')
$ dd if=encrypted_assertion.bin of=edata.bin bs=16 skip=1
324+0 records in
324+0 records out
5184 bytes transferred in 0.002784 secs (1862219 bytes/sec)
$ openssl enc -aes-128-cbc -iv $ivhex -kfile key.pem -nosalt -in edata.bin -out cdata.bin
My efforts in Python were also unfruitful and lead to
ValueError: Ciphertext length must be equal to key size.
I'm going to skip over my efforts in Python unless someone explicitly asks for them but instead hope for a solution using openssl. I know the key is correct because of the successful decryption using samltool.com. How do I decrypt the SAML assertion locally?