We have an exe file that our members have been using. It was submitted to VirusTotal and it returned one red flag: 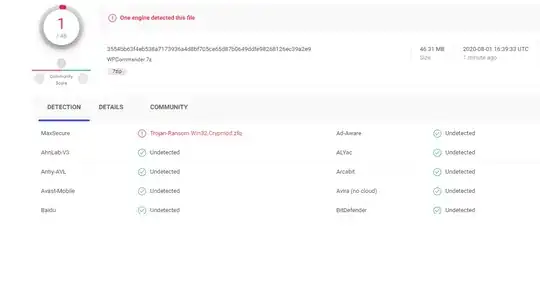
How can we have the app evaluated by a 3rd party software engineer? And how likely is it the app can be evaluated accurately?
I wouldn't worry about a non-well-reputed anti-virus software's findings in comparison to other well established anti-virus vendors. Even with the reputable ones, it could be a false-positive. Vendors themselves sets the scan settings in VirusTotal and some may choose aggressive settings like, heuristics.
If you know the source of the app (i.e. the developer/vendor), you can compare the app's signature (MD5, SHA-1, etc) to the official release. You can see them in the Details table of the VirusTotal result. If it matches, then you know it is the same as the official release.
But, this does not solve the trust problem, if you do not trust the developer/vendor. The app could be malicious and seeing all greens on VirusTotal may mean nothing. Anti-virus software works based on 'virus signature'. If it is a new virus, none of the signatures will match. The next step is the heuristics and behavior analytics, and that works only so far and thus seeing all greens may not mean much for a very new virus (or a very rare virus) if it is good in stealth-mode.
It's true that VirusTotal shares samples with their security partners as mentioned by @nobody. If a file is detected by one vendor, all other non-detecting vendors receives the sample. But with so many false-positives, I don't expect a dedicated analyst to take a look at the file flagged by a non-reputable source. (My experience with them over the years is that it's normal to see 1 or 2 red flags from them.). But, if the file raises some flags through their automated internal tools, then an analyst would review. That's my guess though. But this article supports my guess, "The manual detection of viruses gave way to automated methods designed to find as many as 250 000 new malware files each day." Also, you can accomplish the same thing by using your preferred vendor's "submit a sample" link. Here is Microsoft's sample submission for example.
You can also search for these signatures in Google, AlientVault, IBM X Force, CrowdStrike etc. and see if there is any match. I just did this in Google and nothing came up. That suggests, this is either a brand new file or a custom file you made. If it is a custom ZIP, which I suspect, upload the main file (or all suspect executable), get its signature and for search that. You will see much more details (when first see, activites when run in sandbox, etc) in VirusTotal when you do that.
There are companies that specializes in analyzing malware but it will not be cheap. You can try any of the well known anti-virus companies or an incident response firm like Carbon Black or FireEye and see how much they will charge you for a custom analysis.
If the cost is an issue, you can consider the following
Use CrowdStrike's CrowdInspect tool and see if it will pick anything suspicious on this app while it is being used.
Use AlientVaults free end point scan tool to scan your computer. It uses known IOCS (indicator of compromise) in its database contributed by many companies and individuals (open threat intelligence community)
If you are suspecting it is communicating with a malicious IP (like command and control server) and if that's all you care, you can listen to network requests from this app. If you're well versed in this, you can use free Wireshark tool. If you're not so much into this, then you can use easy to use Microsoft Sysinternal's free ProcMon tool. With ProcMon, just filter for the network event category & just for the process running for this app and monitor which IPs it is going (let it run for a week maybe). ProcMon can resolve the IPs to domain names too if you prefer (useless if resolving to a cloud provider like AWS). But, if this app is running other apps (like browser in headless mode), then you will need to listen all network events for all processes (which can be a tedious task) or first analyze what other processes it accesses to (by letting ProcMon to run with process events selection for let's say for a week). You can have someone do this part with ProcMon or Wireshark for much much less money b/c almost all security professionals and many regular IT people knows how to use these tools but very few knows how to analyze a malware executable and its code (very specialized task).
By default any file/URL submitted to VirusTotal which is detected by at least one scanner is sent to all those scanners that do not detect the resource. So there is a good chance that malware analysts at some of the anti-virus firms will give the file a look, and if it is malicious they will add signatures for it to their scanners. Try waiting a day or so and then reanalyze the file on VirusTotal. If any new engines detect it, the file is likely malicious. Otherwise, a single detection from an obscure anti-virus is probably a false positive.
The detection in your screenshot is from an uncommon antivirus program. There’s also only one detection from over 50 total scanners on VirusTotal. If it was detected by a well known engine like Kaspersky or Microsoft (etc., there are lots of respected ones) it might be worth worrying some more.
So what can you do now?
I used these guys for a few things, I liked it so they are my go-to now. https://www.hybrid-analysis.com/
Another option might possibly be a college or University with a computer science program. No guarantees but they might be willing to have students take a look at it if it pertains to a field of study they are involved in.