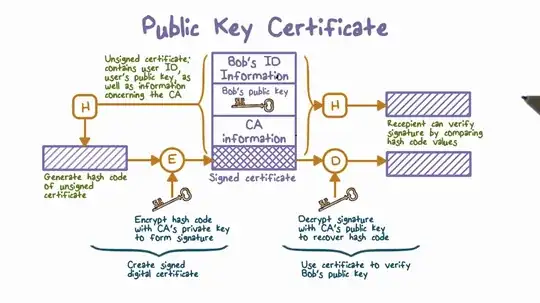
Here is what I understand about how clients trust the tcp channels they are connected to.
- Alice asks Bob for his certificate, signed by a CA's private key
- Bob sends the certificate, which includes his common name (domain or ip) and an attached signed version of it.
- Alice uses her local public key from the CA to decrypt the signed version and compares it to the certificate to verify Bob's claims.
- If it checks out, if it's equal, the tcp layer she is connected to does indeed have Bob at the other end.
- Now that the connection has been verified, both can agree on keys to encrypt their communications.
But couldn't an ISP easily intercept and alter all communications to Bob through a proxy setup just for him inside a network switch? Including sending and receiving the certificate to Alice? Bob's communications already go through network switches, that's where his IP actually lives. An ISP could just inject software right in there to do whatever, as if it was Bob, and no one would know.
Furthermore, the whole process can be compromised at every stage, from the moment Bob sends a CSR to a CA.