I hope this is the Right Place
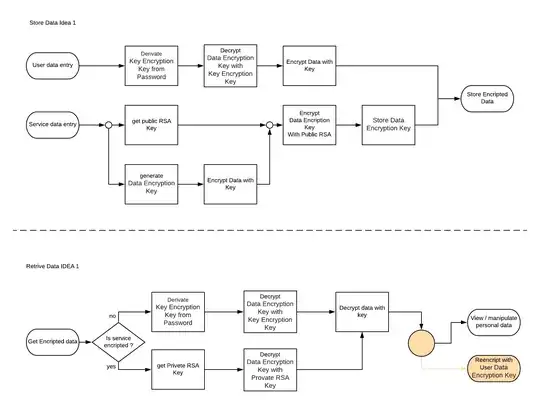
I have implemented a full user encrypted data storage solution. This works well and I can sleep well in the knowledge that neither I nor anyone else except the user can access the data ( AES 265 encrypted should hold for a while). All thanks to you guys. Here is an honorable backlink to the used Algorithm: Store encrypted user data in database
Now to the problem. The customer no longer wants to manually pass the data into the storage and proposed that we integrate with two (my guess is the number will grow) external services that are trusted by the user and should, on behalf of the user, deliver additional data into our database.
How can this be realized without fully butcher the security existing in my current solution?
Currently, I have two ideas on how to resolve this situation:
- Each User has an RSA key pair as well (The Private key is also encrypted like the Data Encryption Key).
- The Service generates a new Data Encryption Key for each user and request pair and encrypts that with the Public RSA key
- The encrypted password will be stored until the user logs in and then re-encrypted
This was the best solution I came up with so far. But not all users are regular and I am sure some will use the automation provided and use the service as a secure drop off place (which I do not mind) but I threaten the RSA security over time. Or maybe I am overengineering and the orange part is not necessary at all.
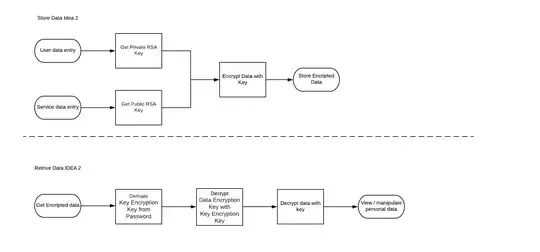
- I switch my whole AES encryption to RSA with a very high bit rate 15'000+. And eat the performance loss
This seems like an easy but not very future proof solution. given the emergence of quantum computers
Any thoughts on my ideas and any help are greatly appreciated
EDIT I was asked to provide some more context. My customers store highly personalized data which makes user identification and tracking extremely easy and is valued by other companies for data mining. Since a data leak can result in personal damage as well as in some cases loss of face. I and my customers value a higher encryption standard to keep their data firmly in their control.
The Services are preidentified and then confirmed/trusted per user. They communicate over an https secured connection but with no further added security. They will push data to the secure storage and then drop the data or secure it internally. No user session /interaction is required. The data they provide is gaining value in conclusion with the rest of the data stored in my system or over a large period of time. But since I expect the number of integrated services will grow so will the worth of the data overall services -> that's why I am interested in fully restricting the access to the user.