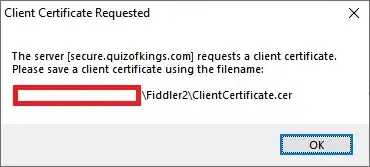
I'm trying to find out a specific request from an android application to its API server. Using Burp Suite, I get a handshake failure alert. Using fiddler it asks me to provide a custom certificate.
Now I have used apktool to de-compile the application, and I have found these files:
- arsalan-ha.quizofkings.com.pem
- certificate.crt
- private_key.pfx
- root-ca.crt
- x1.pfx
But they don't look like certificates. They are secrets used to generate certificates most likely, if I'm correct.
I've uploaded the files here
Could I use these secrets (if they are), to generate certificates and try one by one?