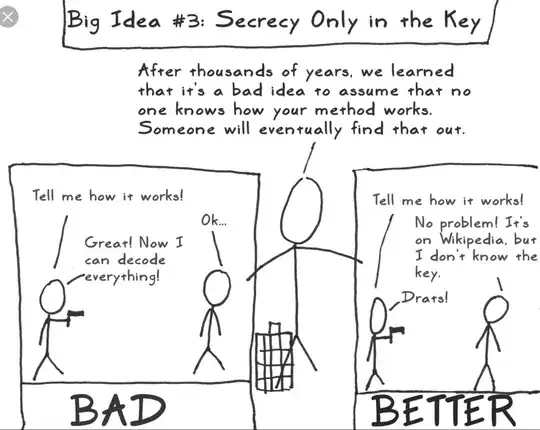
So I was thinking, if people get access somehow to your list of hashes, it's easy for them to figure out what alghoritm you used if they have 32, 40, 60 characters etc
But what if you slice those strings a bit, like you use SHA-1 which is 40 and slice it to 32 characters? That would certainly make people think you are using MD5 and they will be wasting their time using md5 to find out the passwords :))
Would this improve security or have the opposite effect?