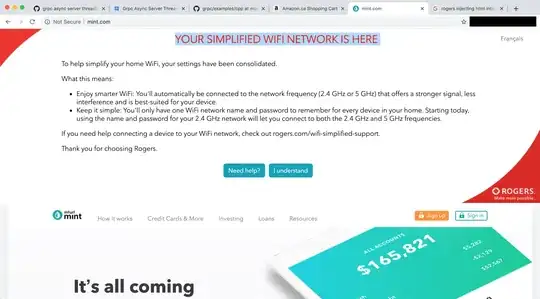
Lately I've noticed that pages I go to on http sometimes have a large banner at the top from my ISP. What's weird is when I refresh the pages I get the https version of the site and the banner is not there. I try to type the http version into the address bar but when I click enter I get the https version. The network tab in developer tools shows 301 moved permanently when putting in the http version and then I get redirected the https version.
So I'm a bit surprised by how I get this banner. How is the ISP able to inject the banner + display the original site underneath the banner? See below screenshot. I would have assumed that the fact the page was redirected to https, that an ISP wouldn't be able to display the page with a banner? What's going on here?
Note: My dns defaults to 1.1.1.1 and 1.0.0.1 (both cloudflare)