I have the following setting: 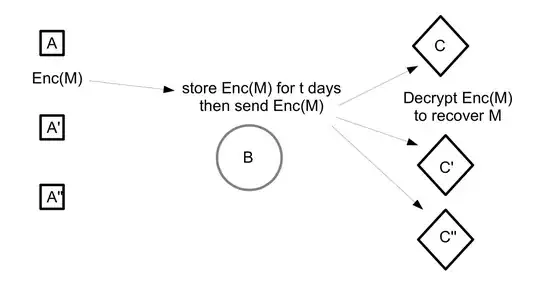 Let A, A', A'' be different mobile devices. They want to sent a secret message M to all (or some of) the C,C', C''. The message is passed on to B that stores it for some time, and passes is on to the different C.
Let A, A', A'' be different mobile devices. They want to sent a secret message M to all (or some of) the C,C', C''. The message is passed on to B that stores it for some time, and passes is on to the different C.
Now I am looking for an encryption scheme, such that A encrypts the message, and only the different C can decrypt it.
My first idea was to simply use the public keys of the different C. However, since B stores the encrypted messages for some time, and we have many copies of the message encrypted with the different private keys, this would not be efficient in terms of storage.
My next idea was to use a common key for the A and C, so that the message is encrypted with this secret key, and then passed on to B that does not posses this key. However, in this case I have the problem of how to generate a secret key between all these participants, that only communicate via B, and how to I handle the situation when a new A or C joins in.
Another idea is to use commutative encryption. However in this case the A and C will depend on the trustworthiness of B. Let A encrypt the message with the key of B, then B stores it encrypted. Then it encrypts it with the public keys of the C and decrypts with its own secret key. B never actually saw the message, would however been able to do so.
What will be the easiest scheme, so that we can easily update all key material, can easily have devices join in and store only one encrypted version of the secret messages without B being able to read it? Is there any efficient multi-party-encryption scheme with an easy handling of the key-material?
I was already referred to the Signal scheme. I am however lost in the scheme amount of algorithms they use. And I think the key-update process in my setting would be more complex, since all communication must pass by B.
If anyone understands my confusing explanation and has some idea of how I can solve this, any help or hint would be very much appreciated!
All the best,
Luca