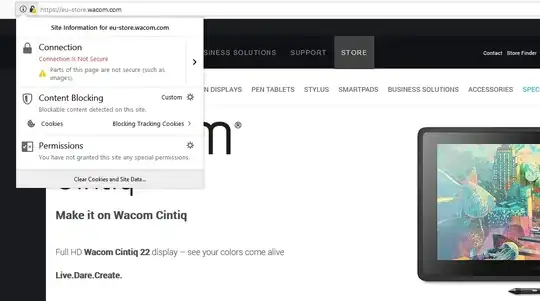
On eu-store.wacom.com, some images from their Amazon CDN are requested over http instead of https
Let me continue from that. Firefox says it's not 100% secure because it's loading unprotected content. I would say, naively... it's 95% secure
Now, it doesn't mean the site wacom.com is not legitimate, but perhaps misconfigured. If you buy today from that site, it's not likely that you are paying a scammer pretending to be Wacom, but see later.
On the contrary, unprotected content served over http can be a danger to Wacom themselves who did not configure their store correctly.
Apart from what government-level attackers can do, here are some examples of what a real attacker can do on a MitM attack over plain old http:
- Images served over http may display something else than the product you are going to buy
- Javascript (and possibly CSS) served over http can be altered and cause any possible harm, including sniffing your credit card number
Iframes served over http can be altered and cause a number of damages, but probably not sniff your CC number (correct me if I am wrong)
Of course I am speaking from a more protocol-theoretical PoV.
So...
how can I verify that the store page is indeed wacom's?
Yes, they are them. The site is not compromised, but vulnerable
is it safe for me to purchase stuff with my card through it
Probably from your home network. I would always avoid sensitive browsing over public wifis or Tor without proper encryption