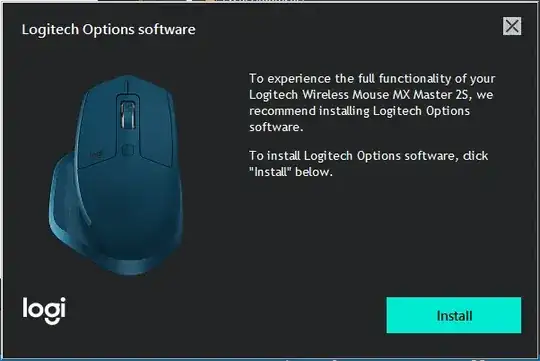
I recently purchased a Logitech MX Master 2S mouse. I had no intention of installing the "options software" that came with the mouse. I simply desired a wireless mouse that wasn't cheap and flimsy.
However, after immediately plugging in the wireless USB dongle, some manner of custom software was able to run without my consent, displaying the following window above all other windows:
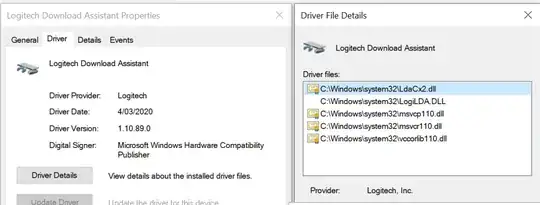
There is no USB volume listed in File Explorer, and to my knowledge autorun from USB is disabled. I was also unable to find an obvious process listed in the Task Manager.
How did this process start? Additionally this seems like an ideal attack vector for Windows machines. Can anyone provide some insight as to how the USB dongle (with no volume) can do this?
Update:
There does not appear to be any built-in logical disk within the dongle, as running wmic logicaldisk get name and diskpart> list volume revealed no additional drives or partitions.